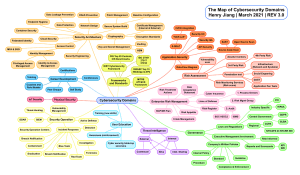
Cybersecurity: People, Process, & Technology for Insider Threat Protection
Anuncio

People, process & technology together protects an organization against the insider threat. As organizations, is necessary start to wake up to the importance of internal security and gain a better understanding of how to stay secure online in both a personal and a work capacity, because in the future, the average employee will hopefully be better educated on security. Security technology will play a big part in this but so will media, culture and education. We will still need IT solutions to secure data and networks in enterprises, but this better user understanding should help its effectiveness. Security has to be a balance of technology and organizational culture. Fortunately, technology can be used to address culture by helping to educate users and encourage good behavior. An example of this would be reminding users of policy at opportune times, like when they are accessing the network outside of normal working hours. If you set up restrictions on network access that force users to act within the limits of your security policy that should come with education on why those restrictions are in place. Once users understand they will be more empowered to follow them of their own conviction. Presumably, we are tired of hearing or reading the popular phrase: "A chain is as strong as its weakest link" Well, in the context of cybersecurity, we can bring the simile of the links considering each of them as the last and most advanced technological device for prevention, as well as for the protection of information so, with which one of them fails, security could be compromised. To this comparison, it should be added that the user is one more link in the chain and possibly the weakest. That is why if a company want workers to become a strong link in the chain, it must give them the importance they deserve. It should be borne in mind that when it comes to truth, it will be the worker, the end user, the real protagonist, since he will be in charge of managing and using the information systems of the organization. But how do I establish a safety culture in my company? Possibly, developing a culture of safety in an organization may be one of the most complex goals that can be set. It requires detailed planning and continuous actions over time. It is common for workers to see a complication, inconvenience, or discomfort in safety protocols. It is not easy to make employees understand that implementing cybersecurity involves implementing a series of actions and establishing a way of working aimed at ensuring the security of information, the main asset of any organization. Thus, in addition to establishing safety policies, regulations and procedures or monitoring whether or not good practices are met, you will have to opt for training actions on employee safety. Traditionally, organizations have tended to label this type of training as an unnecessary expense that does not add value to the company, since they do not see it translated into benefits in their income statement. At most, we will have seen initiatives related to job protection or the prevention of occupational hazards, but very little related to information security. But if you attend what is indicated as best security practices, you will realize that it is mandatory, by a company, to train employees in matters of personal data security that guarantees a correct management of them. However, as in many situations, not all workers in an organization will require the same level of training. This will depend on your assignments or responsibilities. In this way, technical staff will require a high degree of specialization in security and technologies in this field, while an end user who only handles a small part of the corporate information, will not require training in technical aspects, but in the legal and organizational sphere. In addition, the dizzying evolution in technology requires that technical personnel be in a continuous process of training, especially if the organization has a high degree of technological dependence. In short, it will be essential to be aware of the importance of training our workers in terms of information security. And not only in terms of the protection of personal data, but also from the point of view of all the information that the organization processes, always taking into account the responsibilities that each role plays within the organization: Properly protect the workstation (antivirus, updates, email, access control by roles, etc). Apply physical access controls. Treatment and management of compatible media and mobile devices such as laptops, smartphones, IoT devices. Understand the risks associated with using external websites, public Wi-Fi, third-party applications or downloads and updates not validated by the IT department. Learn how to recognize social engineering attacks and how to avoid them. In security, the possible strategy can be defined from total permissiveness to complete control. Each company chooses what it allows to do and what it prohibits in its policies. Having the different policies, rules and procedures, and instructions that are part of the Security Plan will be the first step in making a record of the importance it has in the way the organization is made. The second step is to ensure that all employees know and respect them, through awareness-raising and awareness-raising sessions and drills. Finally, you must provide the necessary training to those who need it. With all this, you'll have the policies enabled in your employees' human firewall that will complete the security chain for your company. Technology Policies People What is the use of all safety measures at work stations if your employee decides when to follow the rules?