HUAWEI USG6000 V100R001 Full-Snapshot Web UI Typical Configuration Examples(V4.0)
Anuncio

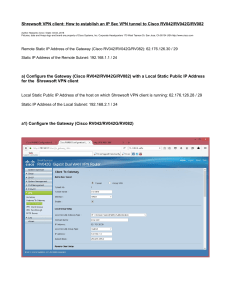
Issue V4.0 Date 2016-01-20 Contents Logging In to the Web Configuration Page 3 Example 1: Accessing the Internet Using a Static IP Address 4 Example 2: Accessing the Internet Using PPPoE 11 Example 3: Both Intranet and Internet Users Accessing an Intranet Server 18 Example 4: Site-to-Site IPSec Tunnel 26 Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) 36 Example 6: L2TP over IPSec Access from Clients (VPN Client /Windows/ Mac OS/Android/iOS) 51 Example 7: SSL VPN Tunnel Access (Network Extension) 104 Example 8: User-specific Bandwidth Management 119 Example 9: Application Control (Limiting P2P Traffic and Disabling QQ) 129 Logging In to the Web Configuration Page Networking Diagram 192.168.0.* Default Settings GE0/0/0 192.168.0.1/24 Management Interface GE0/0/0 IP Address 192.168.0.1/24 User Name/Password admin/Admin@123 Network interface Firewall 1 2 Enable the PC to automatically obtain an IP address. 3 Enter https://interface IP address:port on the browser. 6 to 8 10 (or later versions) Enter the user name and password. Example 1: Accessing the Internet Using a Static IP Address Networking diagram All PCs on the LAN are deployed on subnet 10.3.0.0/24. They dynamically obtain IP addresses through DHCP. The static IP address that the enterprise obtains from the carrier is 1.1.1.1, with a 24-bit subnet mask. The enterprise accesses the Internet through the firewall. Item Data Description DNS server 1.2.2.2/24 Obtained from the carrier Gateway IP address 1.1.1.254/24 Obtained from the carrier Example 1: Accessing the Internet Using a Static IP Address Step1 Configure interfaces 2 1 3 5 4 Set WAN interface parameters. 6 Set LAN interface parameters. Example 1: Accessing the Internet Using a Static IP Address Step2 Configure the DHCP service 1 2 3 4 Configure the DHCP service for LAN interface GE1/0/2 to assign IP addresses to PCs on the LAN. Example 1: Accessing the Internet Using a Static IP Address Step3 Configure security policy 2 1 3 4 Permit intranet IP addresses to access the Internet. Example 1: Accessing the Internet Using a Static IP Address Step4 Configure Source NAT 2 1 3 4 5 Configure Source NAT for intranet users to access the Internet using a public IP address. Example 1: Accessing the Internet Using a Static IP Address Step5 Verify the configurations 1. Check the connectivity of GigabitEthernet 1/0/1 (uplink). 1 Check whether the interface is up. Example 1: Accessing the Internet Using a Static IP Address Step5 Verify the configurations 2. Run the ipconfig/all command on the PC, the correct IP addresses of the PC and DNS server are obtained. 3. The PC on the LAN can use domain names to access the Internet. Example 2: Accessing the Internet Using PPPoE Networking diagram All PCs on the LAN are deployed on subnet 10.3.0.0/24. They dynamically obtain IP addresses through DHCP. The firewall, acting as a client, obtains an IP address by dialing up to the carrier's server through PPPoE for Internet access. Item Data Description GigabitEthernet 1/0/1 Security zone: Untrust Obtains an IP address and a DNS address from the PPPoE server (deployed by the carrier) through dial-up. Dial-up user name: user Dial-up password: Password@ GigabitEthernet 1/0/2 IP address: 10.3.0.1/24 Security zone: Trust Uses DHCP to dynamically assign IP addresses to PCs on the LAN. DNS Server 1.2.2.2/24 Obtains the address from the carrier. Example 2: Accessing the Internet Using PPPoE Step1 Configure interfaces 2 1 3 5 4 Set WAN interface parameters. 6 Set LAN interface parameters. Example 2: Accessing the Internet Using PPPoE Step2 Configure the DHCP service 1 2 3 4 Configure the DHCP service for LAN interface GE1/0/2 to assign IP addresses to PCs on the LAN. Example 2: Accessing the Internet Using PPPoE Step3 Configure security policy 2 1 3 4 Permit intranet IP addresses to access the Internet. Example 2: Accessing the Internet Using PPPoE Step4 Configure Source NAT 2 1 3 4 5 Configure Source NAT for intranet users to access the Internet using a public IP address. Example 2: Accessing the Internet Using PPPoE Step5 Verify the configurations 1. Check the connectivity of GigabitEthernet 1/0/1 (uplink). 1 Check whether the interface is up and whether the connection type is PPPoE. Example 2: Accessing the Internet Using PPPoE Step5 Verify the configurations 2. Run the ipconfig/all command on the, the correct IP addresses of the PC and DNS server are obtained. 3. The PC on the LAN can use domain names to access the Internet. Example 3: Both Intranet and Internet Users Accessing an Intranet Server Networking diagram Both intranet users and the FTP server for Internet users reside on subnet 10.3.0.0/24 in the Trust zone. The enterprise uses a fixed IP address provided by the ISP to access the Internet. Both intranet and Internet users use the public IP address 1.1.1.2 and port 2121 to access the FTP server, and intranet users use public IP address 1.1.1.1 to access the Internet. Item Description Data GigabitEthernet 1/0/2 Security zone: Trust - GigabitEthernet 1/0/1 Security zone: Untrust - FTP server Public IP address : 1.1.1.2 Public Port: 2121 - DNS server 1.2.2.2/24 Obtained from the carrier Gateway IP address 1.1.1.254/24 Obtained from the carrier Example 3: Both Intranet and Internet Users Accessing an Intranet Server Step1 Configure interfaces 2 1 3 5 4 6 Set WAN interface parameters. Set LAN interface parameters. Example 3: Both Intranet and Internet Users Accessing an Intranet Server Step2 Configure security policy 2 1 3 4 5 Configure a security policy for intranet users to access the Internet. Configure a security policy for Internet users to access the intranet FTP server. Example 3: Both Intranet and Internet Users Accessing an Intranet Server 2 1 3 4 Step3 Create a NAT address pool Example 3: Both Intranet and Internet Users Accessing an Intranet Server Step4 Configure Source NAT 2 1 3 4 5 6 Configure Source NAT for intranet users to access the Internet using a public IP address. Configure Source NAT for intranet users to access the public IP address of the FTP server. Example 3: Both Intranet and Internet Users Accessing an Intranet Server 2 1 3 4 Map the private IP address of the FTP server to public IP address 1.1.1.2. Step5 Configure Server Mapping Example 3: Both Intranet and Internet Users Accessing an Intranet Server 1 3 2 4 Step6 Configure NAT ALG Example 3: Both Intranet and Internet Users Accessing an Intranet Server Step7 Verify the configurations 1. The PC on the LAN can access the Internet. 2. Internet users can access public IP address 1.1.1.2 and port 2121 of the FTP server. 3. Intranet users can access public IP address 1.1.1.2 and port 2121 of the FTP server. Example 4: Site-to-Site IPSec Tunnel Networking diagram Firewall_A and Firewall_B are egress gateways of Network A and Network B respectively. Firewall_A and Firewall_B use fixed IP addresses to access the Internet. Firewall_A and Firewall_B establish site-to-site IPSec tunnels in IKE negotiation mode so that the devices on both Network A and Network B can proactively initiate connections to the peer network. Item Firewall_A Firewall_B Scenario Site-to-Site Site-to-Site Peer IP Address 1.1.5.1 1.1.3.1 Authentication Type Pre-Shared Key Pre-Shared Key Pre-Shared Key Admin@123 Admin@123 Local ID IP Address IP Address Peer ID IP Address IP Address Example 4: Site-to-Site IPSec Tunnel Step1 Configure the interfaces on Firewall_A. 1 2 3 5 4 6 Set WAN interface parameters. Set LAN interface parameters. Example 4: Site-to-Site IPSec Tunnel Step2 Configure security policies on Firewall_A. 2 1 3 5 4 Permit private IP addresses on Network B to connect to the private IP addresses on Network A. Permit private IP addresses on Network A to connect to the private IP addresses on Network B. 6 Permit Firewall_B to use its public IP address to connect to Firewall_A. 7 Permit Firewall_A to connect to the public IP address of Firewall_B. Example 4: Site-to-Site IPSec Tunnel Step3 Configure routes on Firewall_A. 1 2 3 4 Configure a route to private IP addresses on Network B. In the example, the next-hop IP address from Firewall_A to the Internet is 1.1.3.2. Example 4: Site-to-Site IPSec Tunnel Step4 Configure IPSec on Firewall_A. In the example, all IPSec proposal parameters use the default values. If you have specific requirements on these parameters, change them, but ensure that they are consistent with those on Firewall_B. 1 3 4 Select a scenario and complete basic settings. 2 5 6 Add a data flow to be encrypted. 7 8 Configure an IPSec proposal. Example 4: Site-to-Site IPSec Tunnel Step5 Configure the interfaces on Firewall_B. 1 2 3 5 4 6 Set WAN interface parameters. Set LAN interface parameters. Example 4: Site-to-Site IPSec Tunnel Step6 Configure security policies on Firewall_B. 2 1 3 5 4 Permit private IP addresses on Network A to connect to the private IP addresses on Network B. Permit private IP addresses on Network B to connect to the private IP addresses on Network A. 6 Permit Firewall_A to use its public IP address to connect to Firewall_B. 7 Permit Firewall_B to connect to the public IP address of Firewall_A. Example 4: Site-to-Site IPSec Tunnel Step7 Configure routes on Firewall_B. 1 2 3 4 Configure a route to private IP addresses on Network A. In the example, the next-hop IP address from Firewall_B to the Internet is 1.1.5.2. Example 4: Site-to-Site IPSec Tunnel Step8 Configure IPSec on Firewall_B. In the example, all IPSec proposal parameters use the default values. If you have specific requirements on these parameters, change them, but ensure that they are consistent with those on Firewall_A. 1 3 4 Select a scenario and complete basic settings. 2 5 6 Add a data flow to be encrypted. 7 8 Configure an IPSec proposal. Example 4: Site-to-Site IPSec Tunnel Step9 Verify the configurations. After the configuration is complete, view the IPSec policy list and IPSec tunnel monitoring information. You can view the established IPSec tunnel. Use a host on Network A to access a host or server on Network B. The access succeeds. Use a host on Network B to access a host or server on Network A. The access also succeeds. IPSec policy list and IPSec tunnel monitoring information on Firewall_A IPSec policy list and IPSec tunnel monitoring information on Firewall_B After the configuration is complete, if no IPSec tunnel is established, click Diagnose to check for the cause and solution. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) Networking diagram Firewall_A is the egress gateway of the headquarters. Firewall_B and Firewall_C are egress gateways of branches 1 and 2, respectively. Firewall_A uses a fixed IP address to access the Internet. Firewall_B and Firewall_C use dynamically obtained IP addresses to access the Internet. IPSec tunnels are established between Firewall_A and Firewall_B and between Firewall_A and Firewall_C, so that PCs in branches 1 and 2 can initiate connections to the headquarters (the headquarters is not allowed to initiate connections to branches). Item Firewall_A (Headquarters) Firewall_B (Branch 1) Firewall_C (Branch 2) Scenario Site-to-Multisite Site-to-Site Site-to-Site Peer IP Address - 1.1.3.1 1.1.3.1 Authentication Type Pre-Shared Key Pre-Shared Key Pre-Shared Key Pre-Shared Key Admin@123 Admin@123 Admin@123 Local ID IP Address IP Address IP Address Peer ID any IP Address IP Address Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) Step1 Configure the interfaces on Firewall_A. 1 2 3 5 4 6 Set WAN interface parameters. Set LAN interface parameters. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) Step2 Configure security policies on Firewall_A. . 2 1 3 4 5 Allow the private IP address of the headquarters to access the private IP addresses of branches 1 and 2. 6 Allow the public IP addresses of branches 1 and 2 to access Firewall_A. As the public IP addresses of the branches are dynamic, no source address is specified. Allow the private IP addresses of branches 1 and 2 to access the private IP address of the headquarters. 7 Allow Firewall_A to access the public IP address of branches 1 and 2. As the public IP addresses of the branches are dynamic, no destination address is specified. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) Step3 Configure routes on Firewall_A. 1 2 3 4 5 Configure a route to private IP addresses of the branch 1. In the example, the next-hop IP address from Firewall_A to the Internet is 1.1.3.2. Configure a route to private IP addresses of the branch 2. In the example, the next-hop IP address from Firewall_A to the Internet is 1.1.3.2. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) Step4 Configure IPSec on Firewall_A. 1 3 4 Configure an IPSec policy. 2 6 Add the data flow (from the headquarters to branch 1) to be encrypted. 7 Add the data flow (from the headquarters to branch 2) to be encrypted. 5 If the static routes to branches are not configured based on step 3, select Reverse Route Injection in the Data Flow to Be Encrypted area, so that the private routes from the headquarters to branches are automatically generated. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) 2 Step5 Configure the interfaces on Firewall_B. 1 3 5 4 Configure the interface connecting to the Internet. In this example, the connection type is DHCP. 6 Set LAN interface parameters. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) Step6 Configure security policies on Firewall_B. . 2 1 3 4 5 Allow the private IP address of branch 1 to access the private IP address of the headquarters. 6 Allow the public IP address of the headquarters to access Firewall_B. As the public IP address of branch 1 is dynamic, no destination address is specified. Allow private IP address of the headquarters to access the private IP address of branch 1. 7 Allow Firewall_B to access the public IP address of the headquarters. As the public IP address of branch 1 is dynamic, no source address is specified. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) 1 2 3 4 Configure a route to the private address of the headquarters. Step7 Configure routes on Firewall_B. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) 1 This example uses the default values of proposal parameters. You can change the values as required. 3 4 Select a scenario and complete basic settings. 2 5 6 Add the data flow (from branch 1 to the headquarters) to be encrypted. 7 Step8 Configure IPSec on Firewall_B. 8 Configure an IPSec proposal. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) 2 Step9 Configure the interfaces on Firewall_C. 1 3 5 4 Configure the interface connecting to the Internet. In this example, the connection type is DHCP. 6 Set LAN interface parameters. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) Step10 Configure security policies on Firewall_C. . 2 1 3 4 5 Allow the private IP address of branch 2 to access the private IP address of the headquarters. 6 Allow the public IP address of the headquarters to access Firewall_C. As the public IP address of branch 2 is dynamic, no destination address is specified. Allow private IP address of the headquarters to access the private IP address of branch 2. 7 Allow Firewall_C to access the public IP address of the headquarters. As the public IP address of branch 2 is dynamic, no source address is specified. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) 1 2 3 4 Configure a route to the private address of the headquarters. Step11 Configure routes on Firewall_C. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) 1 This example uses the default values of proposal parameters. You can change the values as required. 3 4 Select a scenario and complete basic settings. 2 5 6 Add the data flow (from branch 2 to the headquarters) to be encrypted. 7 Step12 Configure IPSec on Firewall_C. 8 Configure an IPSec proposal. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) After the configuration is complete, query the IPSec policy list and IPSec monitoring list. The established IPSec tunnels are displayed. Use a PC in a branch to access a PC or server at the headquarters. The access succeeds. Query the IPSec policy list and IPSec monitoring list on Firewall_A. Step 13 Verify the configuration (1). If the IPSec tunnels are not successfully established, click Diagnose to query the cause and solution. Example 5: Site-to-Multisite IPSec Tunnel (Policy Template) Query the IPSec policy list and IPSec monitoring list on Firewall_B. Query the IPSec policy list and IPSec monitoring list on Firewall_C. Step 13 Verify the configuration (2). Example 6.1: L2TP over IPSec Access from Clients (VPN Client) Networking diagram The LAC client connects to the LNS at the headquarters over the Internet. The LAC client is required to initiate a connection request directly to the LNS, and the communication data with the LNS is transmitted through a tunnel. Firstly, L2TP is used to encapsulate the Layer-2 data for identity authentication, and then IPSec is used to encrypt the data. Trust Headquarters Untrust GE0/0/3 10.1.1.1/24 GE0/0/1 1.1.1.2/24 LAC Client 3.3.3.3/24 Firewall (LNS) Server L2TP over IPSec Tunnel Item LNS LAC client Data L2TP settings Group name: default User name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Local ID: IP address Peer ID: any peer ID Address pool 10.1.2.2 to 10.1.2.100 Ensure that the devices at the headquarters are routable to the addresses in the address pool. The next hop is the LAN interface (GE0/0/3) on the firewall connecting to the headquarters. IP address 3.3.3.3/24 L2TP settings User authentication name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Peer address: 1.1.1.2 Example 6.1: L2TP over IPSec Access from Clients (VPN Client) 2 Step 1 Configure interfaces. 1 3 5 6 4 Set WAN interface parameters. Set LAN interface parameters. Example 6.1: L2TP over IPSec Access from Clients (VPN Client) Step2 Configure security policies. 1 2 3 4 Permit servers at the headquarters to access the Internet. 6 5 Permit LAC clients to access the servers in the headquarters. 7 Permit LAC clients to communicate with the firewall. Permits the firewall to communicate with LAC clients. Example 6.1: L2TP over IPSec Access from Clients (VPN Client) Step 3 Configure L2TP users. 1 3 2 4 Example 6.1: L2TP over IPSec Access from Clients (VPN Client) 1 3 2 5 4 6 Step 4 Configure L2TP over IPSec. Example 6.1: L2TP over IPSec Access from Clients (VPN Client) Step 5 Configure the VPN client. In the example, the VPN Client version is V100R001C02SPC700. 1 Open the Secoway VPN Client software and create a connection. 2 3 Enter the IP address of the WAN interface on the firewall. 4 Enter the pre-shared key specified on the firewall. In the example, enter Admin@123. Example 6.1: L2TP over IPSec Access from Clients (VPN Client) 5 Step 5 Configure the VPN client. 6 7 8 Example 6.1: L2TP over IPSec Access from Clients (VPN Client) Step 5 Configure the VPN client. 10 9 Set the DNS server address for Internet access. Add a route to the VPN network segment. Example 6.1: L2TP over IPSec Access from Clients (VPN Client) Step 5 Configure the VPN client. 1 2 Status after the VPN connection is established Example 6.1: L2TP over IPSec Access from Clients (VPN Client) 3 IPSec tunnel information displayed on the firewall 4 L2TP tunnel information displayed on the firewall Step 6 Verify the configurations. Example 6.2: L2TP over IPSec Access from Clients (Windows 7) Networking diagram The LAC client connects to the LNS at the headquarters over the Internet. The LAC client is required to initiate a connection request directly to the LNS, and the communication data with the LNS is transmitted through a tunnel. Firstly, L2TP is used to encapsulate the Layer-2 data for identity authentication, and then IPSec is used to encrypt the data. Trust Headquarters Untrust GE0/0/3 10.1.1.1/24 GE0/0/1 1.1.1.2/24 LAC Client 3.3.3.3/24 Firewall (LNS) Server L2TP over IPSec Tunnel Item LNS LAC client Data L2TP settings Group name: default User name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Local ID: IP address Peer ID: any peer ID Address pool 10.1.2.2 to 10.1.2.100 Ensure that the devices at the headquarters are routable to the addresses in the address pool. The next hop is the LAN interface (GE0/0/3) on the firewall connecting to the headquarters. IP address 3.3.3.3/24 L2TP settings User authentication name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Peer address: 1.1.1.2 Example 6.2: L2TP over IPSec Access from Clients (Windows 7) 2 Step 1 Configure interfaces. 1 3 5 6 4 Set WAN interface parameters. Set LAN interface parameters. Example 6.2: L2TP over IPSec Access from Clients (Windows 7) Step2 Configure security policies. 1 2 3 4 Permit servers at the headquarters to access the Internet. 6 5 Permit LAC clients to access the servers in the headquarters. 7 Permit LAC clients to communicate with the firewall. Permits the firewall to communicate with LAC clients. Example 6.2: L2TP over IPSec Access from Clients (Windows 7) Step 3 Configure L2TP users. 1 3 2 4 Example 6.2: L2TP over IPSec Access from Clients (Windows 7) 1 3 2 5 4 6 Step 4 Configure L2TP over IPSec. Example 6.2: L2TP over IPSec Access from Clients (Windows 7) Step 5 Configure the LAC client. 1 Access the control panel. 2 3 Create a VPN connection. Example 6.2: L2TP over IPSec Access from Clients (Windows 7) 4 Step 5 Configure the LAC client. 5 7 8 6 Example 6.2: L2TP over IPSec Access from Clients (Windows 7) 11 10 Right-click the connection and select Properties. 9 Click on the lower right of the desktop. Step 5 Configure the LAC client. 12 Example 6.2: L2TP over IPSec Access from Clients (Windows 7) 1 2 Step 6 Verify the configurations. Example 6.2: L2TP over IPSec Access from Clients (Windows 7) 3 IPSec tunnel information displayed on the firewall 4 L2TP tunnel information displayed on the firewall Step 6 Verify the configurations. Example 6.3: L2TP over IPSec Access from Clients (Windows 8) Networking diagram The LAC client connects to the LNS at the headquarters over the Internet. The LAC client is required to initiate a connection request directly to the LNS, and the communication data with the LNS is transmitted through a tunnel. Firstly, L2TP is used to encapsulate the Layer-2 data for identity authentication, and then IPSec is used to encrypt the data. Trust Headquarters Untrust GE0/0/3 10.1.1.1/24 GE0/0/1 1.1.1.2/24 LAC Client 3.3.3.3/24 Firewall (LNS) Server L2TP over IPSec Tunnel Item LNS LAC client Data L2TP settings Group name: default User name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Local ID: IP address Peer ID: any peer ID Address pool 10.1.2.2 to 10.1.2.100 Ensure that the devices at the headquarters are routable to the addresses in the address pool. The next hop is the LAN interface (GE0/0/3) on the firewall connecting to the headquarters. IP address 3.3.3.3/24 L2TP settings User authentication name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Peer address: 1.1.1.2 Example 6.3: L2TP over IPSec Access from Clients (Windows 8) 2 Step 1 Configure interfaces. 1 3 5 6 4 Set WAN interface parameters. Set LAN interface parameters. Example 6.3: L2TP over IPSec Access from Clients (Windows 8) Step2 Configure security policies. 1 2 3 4 Permit servers at the headquarters to access the Internet. 6 5 Permit LAC clients to access the servers in the headquarters. 7 Permit LAC clients to communicate with the firewall. Permits the firewall to communicate with LAC clients. Example 6.3: L2TP over IPSec Access from Clients (Windows 8) Step 3 Configure L2TP users. 1 3 2 4 Example 6.3: L2TP over IPSec Access from Clients (Windows 8) 1 3 2 5 4 6 Step 4 Configure L2TP over IPSec. Example 6.3: L2TP over IPSec Access from Clients (Windows 8) 1 Step 5 Configure the LAC client. 3 4 Open network connection. 2 5 6 Enter the IP address of the WAN interface on the firewall. Example 6.3: L2TP over IPSec Access from Clients (Windows 8) Step 5 Configure the LAC client. 8 9 7 Click Connections, right-click a specific connection, and select View connection properties. Enter the pre-shared key specified on the firewall. In the example, enter Admin@123. Example 6.3: L2TP over IPSec Access from Clients (Windows 8) Step 6 Verify the configurations. 1 2 Enter the user name and password. Status after the VPN connection is established Example 6.3: L2TP over IPSec Access from Clients (Windows 8) 3 IPSec tunnel information displayed on the firewall 4 L2TP tunnel information displayed on the firewall Step 6 Verify the configurations. Example 6.4: L2TP over IPSec Access from Clients (MAC OS) Networking diagram The LAC client connects to the LNS at the headquarters over the Internet. The LAC client is required to initiate a connection request directly to the LNS, and the communication data with the LNS is transmitted through a tunnel. Firstly, L2TP is used to encapsulate the Layer-2 data for identity authentication, and then IPSec is used to encrypt the data. Trust Headquarters Untrust GE0/0/3 10.1.2.1/24 GE0/0/1 1.1.1.2/24 LAC Client 3.3.3.3/24 Firewall (LNS) Server L2TP over IPSec Tunnel Item LNS LAC client Data L2TP settings Group name: default User name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Local ID: IP address Peer ID: any peer ID Address pool 10.1.1.2 to 10.1.1.100 Ensure that the devices at the headquarters are routable to the addresses in the address pool. The next hop is the LAN interface (GE0/0/3) on the firewall connecting to the headquarters. IP address 3.3.3.3/24 L2TP settings User authentication name: macpc Password: Hello123 IPSec settings Pre-shared key: Admin@123 Peer address: 1.1.1.2 Example 6.4: L2TP over IPSec Access from Clients (MAC OS) 2 Step 1 Configure interfaces. 1 3 5 6 4 Set WAN interface parameters. Set LAN interface parameters. Example 6.4: L2TP over IPSec Access from Clients (MAC OS) Step2 Configure security policies. 1 2 3 4 Permit servers at the headquarters to access the Internet. 6 5 Permit LAC clients to access the servers in the headquarters. 7 Permit LAC clients to communicate with the firewall. Permits the firewall to communicate with LAC clients. Example 6.4: L2TP over IPSec Access from Clients (MAC OS) Step 3 Configure L2TP users. 1 3 2 4 Example 6.4: L2TP over IPSec Access from Clients (MAC OS) 1 3 2 5 4 6 Step 4 Configure L2TP over IPSec. Example 6.4: L2TP over IPSec Access from Clients (MAC OS) Step 5 Configure the LAC client. 1 Create a VPN connection. 4 2 3 Example 6.4: L2TP over IPSec Access from Clients (MAC OS) Step 5 Configure the LAC client. 8 5 6 7 Enter the password of user macpc specified on the firewall. In the example, enter Hello123. Enter the pre-shared key specified on the firewall. In the example, enter Admin@123. Example 6.4: L2TP over IPSec Access from Clients (MAC OS) Step 5 Verify the configurations. Status after the VPN connection is established 1 2 Example 6.4: L2TP over IPSec Access from Clients (MAC OS) 3 IPSec tunnel information displayed on the firewall 4 L2TP tunnel information displayed on the firewall Step 6 Verify the configurations. Example 6.5: L2TP over IPSec Access from Clients (Android) Networking diagram The LAC client connects to the LNS at the headquarters over the Internet. The LAC client is required to initiate a connection request directly to the LNS, and the communication data with the LNS is transmitted through a tunnel. Firstly, L2TP is used to encapsulate the Layer-2 data for identity authentication, and then IPSec is used to encrypt the data. Trust Headquarters Untrust GE0/0/3 10.1.1.1/24 GE0/0/1 1.1.1.2/24 LAC Client 3.3.3.3/24 Firewall (LNS) Server L2TP over IPSec Tunnel Item LNS LAC client Data L2TP settings Group name: default User name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Local ID: IP address Peer ID: any peer ID Address pool 10.1.2.2 to 10.1.2.100 Ensure that the devices at the headquarters are routable to the addresses in the address pool. The next hop is the LAN interface (GE0/0/3) on the firewall connecting to the headquarters. IP address 3.3.3.3/24 L2TP settings User authentication name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Peer address: 1.1.1.2 Example 6.5: L2TP over IPSec Access from Clients (Android) 2 Step 1 Configure interfaces. 1 3 5 6 4 Set WAN interface parameters. Set LAN interface parameters. Example 6.5: L2TP over IPSec Access from Clients (Android) Step2 Configure security policies. 1 2 3 4 Permit servers at the headquarters to access the Internet. 6 5 Permit LAC clients to access the servers in the headquarters. 7 Permit LAC clients to communicate with the firewall. Permits the firewall to communicate with LAC clients. Example 6.5: L2TP over IPSec Access from Clients (Android) Step 3 Configure L2TP users. 1 3 2 4 Example 6.5: L2TP over IPSec Access from Clients (Android) 1 3 2 5 4 6 Step 4 Configure L2TP over IPSec. Example 6.5: L2TP over IPSec Access from Clients (Android) Step 5 Configure the LAC client. 2 4 Enter the IP address of the WAN interface on the firewall. 1 Enter the Settings page and create a VPN connection. Enter the pre-shared key specified on the firewall. In the example, enter Admin@123. 3 In the example, the Android version is Android4.2. Example 6.5: L2TP over IPSec Access from Clients (Android) Step 6 Verify the configurations. 1 2 3 Example 6.5: L2TP over IPSec Access from Clients (Android) 4 IPSec tunnel information displayed on the firewall 5 L2TP tunnel information displayed on the firewall Step 6 Verify the configurations. Example 6.6: L2TP over IPSec Access from Clients (iOS) Networking diagram The LAC client connects to the LNS at the headquarters over the Internet. The LAC client is required to initiate a connection request directly to the LNS, and the communication data with the LNS is transmitted through a tunnel. Firstly, L2TP is used to encapsulate the Layer-2 data for identity authentication, and then IPSec is used to encrypt the data. Trust Headquarters Untrust GE0/0/3 10.1.1.1/24 GE0/0/1 1.1.1.2/24 LAC Client 3.3.3.3/24 Firewall (LNS) Server L2TP over IPSec Tunnel Item LNS LAC client Data L2TP settings Group name: default User name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Local ID: IP address Peer ID: any peer ID Address pool 10.1.2.2 to 10.1.2.100 Ensure that the devices at the headquarters are routable to the addresses in the address pool. The next hop is the LAN interface (GE0/0/3) on the firewall connecting to the headquarters. IP address 3.3.3.3/24 L2TP settings User authentication name: vpdnuser Password: Hello123 IPSec settings Pre-shared key: Admin@123 Peer address: 1.1.1.2 Example 6.6: L2TP over IPSec Access from Clients (iOS) 2 Step 1 Configure interfaces. 1 3 5 6 4 Set WAN interface parameters. Set LAN interface parameters. Example 6.6: L2TP over IPSec Access from Clients (iOS) Step2 Configure security policies. 1 2 3 4 Permit servers at the headquarters to access the Internet. 6 5 Permit LAC clients to access the servers in the headquarters. 7 Permit LAC clients to communicate with the firewall. Permits the firewall to communicate with LAC clients. Example 6.6: L2TP over IPSec Access from Clients (iOS) Step 3 Configure L2TP users. 1 3 2 4 Example 6.6: L2TP over IPSec Access from Clients (iOS) Step 4 Configure L2TP over IPSec. 1 3 2 5 4 6 Example 6.6: L2TP over IPSec Access from Clients (iOS) Step 6 Configure the LAC client. 1 2 3 6 5 Enter the IP address of the WAN interface on the firewall. 4 Enter the pre-shared key specified on the firewall. In the example, enter Admin@123. Example 6.6: L2TP over IPSec Access from Clients (iOS) Step 6 Verify the configurations. 1 Enable VPN. 2 Status after the VPN connection is established. Example 6.6: L2TP over IPSec Access from Clients (iOS) 3 IPSec tunnel information displayed on the firewall 4 L2TP tunnel information displayed on the firewall Step 6 Verify the configurations. Example 7: SSL VPN Tunnel Access (Network Extension) GE0/0/3 Enterprise network 10.1.1.1/24 GE0/0/1 1.1.1.1/24 Teleworker Untrust Networking diagram Firewall DNS Server Trust The enterprise requires that each teleworker have an intranet IP address to access intranet resources as if they were access the resources on the LAN. For security reasons, certificate and local authentication (certificate challenge) should be configured to authenticate teleworkers. Item Data DNS server IP address: 10.1.1.2/24 Domain name: internal.com Authentication mode Certificate challenge Auxiliary authentication mode: VPNDB SSL VPN user User name: user Password: Admin@123 Client certificate user.p12 Import the client certificate to the browser on the device for teleworking. The firewall verifies the user's identity based on the client certificate. The common name in the client certificate must be the same as the SSL VPN user name. Client CA certificate ca.crt The CA server that issues the client certificate has a CA certificate. After being imported to the firewall, this CA certificate is used by the firewall to verify the validity of the client certificate. Virtual IP address pool of network extension 10.1.1.50~10.1.1.100 After the device for teleworking connects to the enterprise network through SSL VPN and enables network extension, the firewall will assign an IP address in the address pool to the device. Example 7: SSL VPN Tunnel Access (Network Extension) 2 Step 1 Configure interfaces. 1 3 5 6 4 Set WAN interface parameters. Set LAN interface parameters. Example 7: SSL VPN Tunnel Access (Network Extension) 1 6 2 4 3 Step 2 Create a user group and its users. Example 7: SSL VPN Tunnel Access (Network Extension) 1 3 2 Step 3 Configure an SSL VPN gateway. Example 7: SSL VPN Tunnel Access (Network Extension) 4 Step 3 Configure an SSL VPN gateway. Example 7: SSL VPN Tunnel Access (Network Extension) 5 Step 3 Configure an SSL VPN gateway. Example 7: SSL VPN Tunnel Access (Network Extension) 6 Step 3 Configure an SSL VPN gateway. Example 7: SSL VPN Tunnel Access (Network Extension) 7 Step 3 Configure an SSL VPN gateway. Example 7: SSL VPN Tunnel Access (Network Extension) Step4 Configure security policies. 1 2 4 3 Permit employees working at home to log in to the SSL VPN gateway. Permit teleworkers to access intranet resources. Do not set the source or destination zone for the policy. Set the source address to the network extension address pool and destination address to the IP address of the intranet resource that teleworkers are allowed to access. Example 7: SSL VPN Tunnel Access (Network Extension) 1 On the PC, open the IE browser. 3 2 Step 5 Install the client certificate. Example 7: SSL VPN Tunnel Access (Network Extension) Step 5 Install the client certificate. Select client certificate user.p12 from the local device and import it to the PC. 5 4 Example 7: SSL VPN Tunnel Access (Network Extension) 6 If a private key password is specified in the certificate, enter the private key password in Password. 7 Step 5 Install the client certificate. Example 7: SSL VPN Tunnel Access (Network Extension) 1 Step 6 Verify the configurations. Enter https://1.1.1.1 on the browser and install the Control. 2 Enter a password and select a certificate. Virtual gateways of different versions require clients to install different versions of Active Control. If a client needs to access a different version of the virtual gateway, delete the old Active Control before accessing the new one. Otherwise, the browser will be stuck on the page for loading the component. If the client is a PC, you can run the following commands to delete the Control: PC> regsvr32 SVNIEAgt.ocx -u -s PC> del %systemroot%\SVNIEAgt.ocx /q PC> del %systemroot%\"Downloaded Program Files"\SVNIEAgt.inf /q PC> cd %appdata% PC> rmdir svnclient /q /s Example 7: SSL VPN Tunnel Access (Network Extension) 3 Network extension status after being enabled Step 6 Verify the configurations. Example 7: SSL VPN Tunnel Access (Network Extension) Step 6 Verify the configurations. Virtual IP address and DNS server address that the client obtains from the firewall. The client can access resources on the enterprise network. For example, the client can ping the DNS server (10.1.1.2) on the enterprise network. Example 8: User-specific Bandwidth Management Networking diagram The highest download traffic rate and maximum number of users are subject to the actual specifications. The web configuration for limiting the upload traffic rate is similar to that for file downloading. This example describes how to limit the file download traffic rate. A firewall is deployed as an egress gateway at the border of an enterprise network. As the traffic rate is limited for users on the enterprise network to access the Internet, congestion likely occurs. Limiting the user traffic rate effectively prevents network congestion. Example 8: User-specific Bandwidth Management Data planning Item Data Description Total network bandwidth 20 Mbps Data must be planned based on the global bandwidth that the operator rents to the enterprise and the number of users who need to access the Internet. 1 Mbps = 1000 kbps = 125 KB/s Senior manager Global guaranteed downlink bandwidth: 2 Mbps Global maximum downlink bandwidth: 6 Mbps Group: Group name: manager/Parent group: default User: User name: user_0001/Group: manager/Authentication type: local authentication - R&D employee Global maximum downlink bandwidth for product groups 1 and 2: 2 Mbps Global maximum downlink bandwidth: 5 Mbps Group: Group name: research/Parent group: default Group name: research_product1/Parent group: research Group name: research_product2/Parent group: research User: User name: user_0002/Group: research_product1/Authentication type: local authentication User name: user_0003/Group: research_product2/Authentication type: local authentication The R&D department has two product groups. Marketing employee Global maximum downlink bandwidth: 5 Mbps Per-user maximum downlink bandwidth: 2 Mbps Group: Group name: marketing/Parent group: default User: User name: user_0004 Group: marketing/Authentication type: local authentication - Example 8: User-specific Bandwidth Management 2 Step 1 Configure interfaces 1 To allow users on the enterprise network to access the Internet, you need to configure a Source NAT policy. For detailed configurations, see “Example 1: Accessing the Internet Using a Static IP Address”. 4 Set parameters for the interface connecting to the Internet. 5 Set interface bandwidth parameters. Limit the total bandwidth to 20 Mbps. 7 Set parameters for the interface connecting to the enterprise network. 3 6 Example 8: User-specific Bandwidth Management Step 2 Configure user groups 1 7 Create a user group for product group 1. 2 3 8 Create a user group for product group 2. 4 5 Create a user group for senior managers. 6 Create a user group for the marketing department. Create a user group for the R&D department. Example 8: User-specific Bandwidth Management Step 3 Configure users You can create multiple users for each user group as required. 1 2 3 7 Create a user for product group 2. 4 5 Create a senior manager user. 6 Create a user for the marketing department. Create a user for product group 1. Example 8: User-specific Bandwidth Management 1 2 3 4 Configure a security policy to allow users in subnet 10.3.0.0/24 of the Trust zone to access the Internet. Step 4 Configure a security policy Example 8: User-specific Bandwidth Management 2 3 Step 5 Configure traffic profiles for intranet users 1 You can set uplink bandwidth parameters based on service requirements, for example, limiting the file upload traffic. 4 Configure a traffic profile to limit the global downlink bandwidth. 5 Configure a traffic profile to limit the per-user maximum downlink bandwidth to 2 Mbps. 6 Configure a traffic profile to limit the global maximum downlink bandwidth to 5 Mbps. 8 Configure a traffic profile to limit the global maximum downlink bandwidth to 2 Mbps. 7 Configure a traffic profile to limit the global maximum downlink bandwidth to 2 Mbps. Example 8: User-specific Bandwidth Management Step 6 Configure traffic policies for intranet users 1 3 2 4 Configure a traffic policy for senior managers. Configure the bandwidth policy based on service requirements. For example, if you want to limit traffic based on IP addresses, specify source and destination address region, not users or user groups. 5 Configure a traffic policy for the marketing department. 8 Configure a traffic policy for product group 2. 6 Configure a traffic policy for the R&D department. 7 Configure a traffic policy for product group 1. Example 8: User-specific Bandwidth Management Step 7 Verify the configuration 1. A senior manager uses FileZilla and FTP tools to download files from the Internet. The download traffic rate should not exceed 6 Mbps. FileZilla-based download is used as an example. Before the configuration, the download traffic rate exceeds 6 Mbps (946.8 KB/s = 7.5744 Mbps). After the configuration, the download traffic rate for the same file ranges from 2 to 6 Mbps (567.0 KB/s = 4.536 Mbps). Before the configuration After the configuration 2. Marketing employees use FileZilla and FTP tools to download files from the Internet. The per-user download traffic rate should not exceed 2 Mbps. FileZilla-based download is used as an example. Before the configuration, the download traffic rate exceeds 2 Mbps (946.8 KB/s = 7.5744 Mbps). After the configuration, the download traffic rate for the same file does not exceed 2 Mbps (177.7 KB/s = 1.4216 Mbps). Before the configuration After the configuration Example 8: User-specific Bandwidth Management Step 7 Verify the configuration 3. Employees in product group 1 use FileZilla and FTP tools to download files from the Internet. The download traffic rate should not exceed 2 Mbps. FileZilla-based download is used as an example. Before the configuration, the download traffic rate exceeds 2 Mbps (946.8 KB/s = 7.5744 Mbps). After the configuration, the download traffic rate for the same file does not exceed 2 Mbps (175.8 KB/s = 1.4064 Mbps). Before the configuration After the configuration 4. Employees in product group 2 use FileZilla and FTP tools to download files from the Internet. The download traffic rate should not exceed 2 Mbps. FileZilla-based download is used as an example. Before the configuration, the download traffic rate exceeds 2 Mbps (946.8 KB/s = 7.5744 Mbps). After the configuration, the download traffic rate for the same file does not exceed 2 Mbps (190.8 KB/s = 1.5264 Mbps). Before the configuration After the configuration Example 9: Application Control (Limiting P2P Traffic and Disabling QQ) Networking Diagram QQ Trust 10.3.0.0/24 Untrust Firewall GE1/0/1 10.3.0.1/24 GE1/0/2 1.1.1.1/24 P2P An enterprise allows employees to access the Internet, but requires to disable chatting software for productivity, such as QQ, and limit the P2P download traffic to 3 Mbps. Item Data Description P2P traffic limiting Maximum bandwidth: 3 Mbps 1 Mbps=1000 kbps=125 KB/s Security policy Block the QQ protocol. - Example 9: Application Control (Limiting P2P Traffic and Disabling QQ) 2 Step1 Configure Interfaces 1 3 To enable intranet users to access the Internet, configure Source NAT policies. For configurations, see "Example 1: Accessing the Internet Using a Static IP Address." 5 6 4 Configure LAN interfaces. Configure WAN interfaces. Example 9: Application Control (Limiting P2P Traffic and Disabling QQ) 1 3 2 4 Set the maximum global downlink bandwidth to 3 Mbps. Step2 Configure Traffic Profile Example 9: Application Control (Limiting P2P Traffic and Disabling QQ) 2 Step3 Configure Traffic Policy 1 3 4 Create a traffic policy to limit P2P download bandwidth within 3 Mbps. FileShare_P2P indicates P2P download, and such P2P applications include BT, eDonkey/eMule, and Thunder. You can limit specific P2P services as required, such as permitting BT download but denying eMule download. Example 9: Application Control (Limiting P2P Traffic and Disabling QQ) 2 1 Step4 Configure Security Policy If multiple security policies are available in one interzone, the device will match the traffic to the policies one by one in the list. After a policy is matched, the matching process stops. Therefore, to ensure that the configurations take effect in case of multiple available security policies, tune the policy priorities and put the most specific one in front of lease specific ones. 3 4 5 Deny QQ for enterprise employees. Allow enterprise employees to access the Internet. Example 9: Application Control (Limiting P2P Traffic and Disabling QQ) 1. Enterprise employees can access the Internet but cannot log in to QQ. The system displays “Network time out. It may be caused by wrong configuration. ” Before configuration After configuration 2. Enterprise employees use tools, such as BT, eDonkey/eMule, and Thunder to download files from the Internet, and the download rate does not exceed 3 Mbps. For example, before configuration, the BT download rate exceeds 3 Mbps (846.6 KB/s=6.77 Mbps). After the configuration is complete, the file download rate is controlled within 3 Mbps (268.5 KB/s=2.148 Mbps). Step5 Verify the Configurations