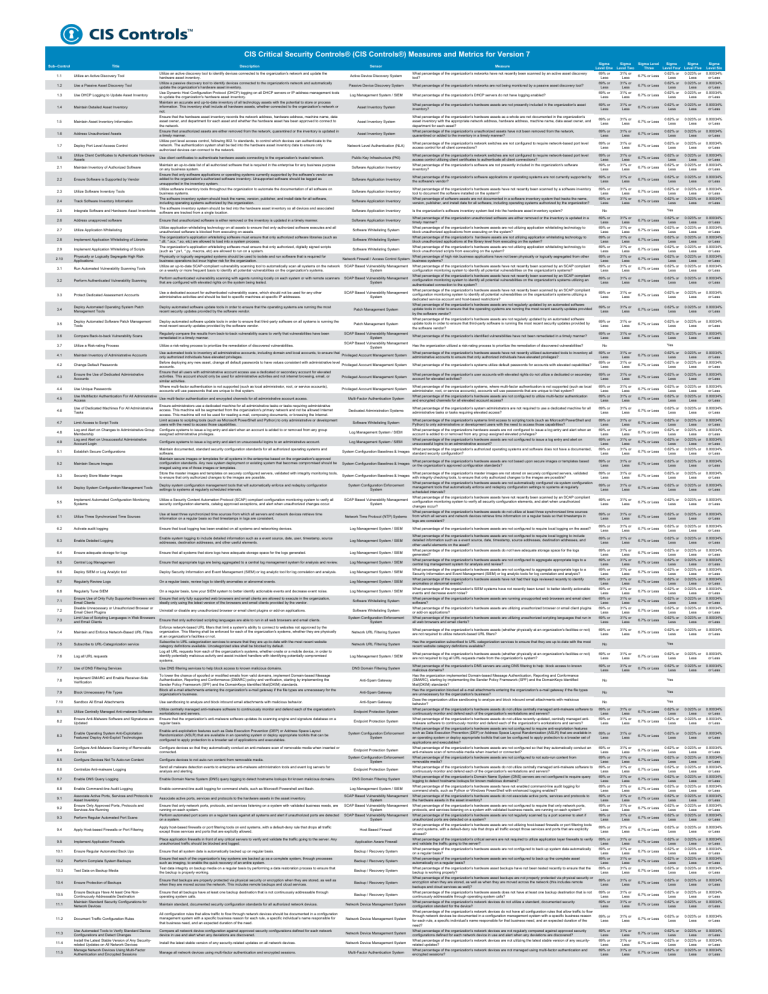
CIS Critical Security Controls® (CIS Controls®) Measures and Metrics for Version 7 Sub--Control Title 1.1 Utilize an Active Discovery Tool 1.2 Use a Passive Asset Discovery Tool 1.3 Use DHCP Logging to Update Asset Inventory 1.4 Maintain Detailed Asset Inventory 1.5 Maintain Asset Inventory Information 1.6 Address Unauthorized Assets 1.7 Deploy Port Level Access Control 1.8 Utilize Client Certificates to Authenticate Hardware Assets 2.1 Maintain Inventory of Authorized Software 2.2 2.3 2.4 2.5 2.6 Description Utilize an active discovery tool to identify devices connected to the organization's network and update the hardware asset inventory. Utilize a passive discovery tool to identify devices connected to the organization's network and automatically update the organization's hardware asset inventory. Use Dynamic Host Configuration Protocol (DHCP) logging on all DHCP servers or IP address management tools to update the organization's hardware asset inventory. Maintain an accurate and up-to-date inventory of all technology assets with the potential to store or process information. This inventory shall include all hardware assets, whether connected to the organization's network or not. Ensure that the hardware asset inventory records the network address, hardware address, machine name, data asset owner, and department for each asset and whether the hardware asset has been approved to connect to the network. Ensure that unauthorized assets are either removed from the network, quarantined or the inventory is updated in a timely manner. Utilize port level access control, following 802.1x standards, to control which devices can authenticate to the network. The authentication system shall be tied into the hardware asset inventory data to ensure only authorized devices can connect to the network. Use client certificates to authenticate hardware assets connecting to the organization's trusted network. Maintain an up-to-date list of all authorized software that is required in the enterprise for any business purpose on any business system. Ensure that only software applications or operating systems currently supported by the software's vendor are added to the organization's authorized software inventory. Unsupported software should be tagged as Ensure Software is Supported by Vendor unsupported in the inventory system. Utilize software inventory tools throughout the organization to automate the documentation of all software on Utilize Software Inventory Tools business systems. The software inventory system should track the name, version, publisher, and install date for all software, Track Software Inventory Information including operating systems authorized by the organization. The software inventory system should be tied into the hardware asset inventory so all devices and associated Integrate Software and Hardware Asset Inventories software are tracked from a single location. Address unapproved software 2.7 Utilize Application Whitelisting 2.8 Implement Application Whitelisting of Libraries 2.9 Implement Application Whitelisting of Scripts 2.10 Physically or Logically Segregate High Risk Applications Ensure that unauthorized software is either removed or the inventory is updated in a timely manner. Sensor Active Device Discovery System Asset Inventory System Asset Inventory System Network Level Authentication (NLA) Public Key Infrastructure (PKI) Software Application Inventory Software Application Inventory Software Application Inventory Software Application Inventory Software Application Inventory Software Application Inventory 3.2 Perform Authenticated Vulnerability Scanning Perform authenticated vulnerability scanning with agents running locally on each system or with remote scanners that are configured with elevated rights on the system being tested. SCAP Based Vulnerability Management System 3.3 Protect Dedicated Assessment Accounts Use a dedicated account for authenticated vulnerability scans, which should not be used for any other administrative activities and should be tied to specific machines at specific IP addresses. SCAP Based Vulnerability Management System 3.4 Deploy Automated Operating System Patch Management Tools Deploy automated software update tools in order to ensure that the operating systems are running the most recent security updates provided by the software vendor. Patch Management System 3.5 Deploy Automated Software Patch Management Tools Deploy automated software update tools in order to ensure that third-party software on all systems is running the most recent security updates provided by the software vendor. Patch Management System 3.6 Compare Back-to-back Vulnerability Scans Regularly compare the results from back-to-back vulnerability scans to verify that vulnerabilities have been remediated in a timely manner. 3.7 Utilize a Risk-rating Process Utilize a risk-rating process to prioritize the remediation of discovered vulnerabilities. 4.1 Maintain Inventory of Administrative Accounts 4.2 Change Default Passwords 4.3 Ensure the Use of Dedicated Administrative Accounts 4.4 Use Unique Passwords 4.6 4.7 4.8 4.9 Maintain documented, standard security configuration standards for all authorized operating systems and software. Maintain secure images or templates for all systems in the enterprise based on the organization's approved configuration standards. Any new system deployment or existing system that becomes compromised should be imaged using one of those images or templates. Store the master images and templates on securely configured servers, validated with integrity monitoring tools, to ensure that only authorized changes to the images are possible. SCAP Based Vulnerability Management System SCAP Based Vulnerability Management System 9.2 Ensure that only network ports, protocols, and services listening on a system with validated business needs, are running on each system. Perform automated port scans on a regular basis against all systems and alert if unauthorized ports are detected on a system. 0.023% or Less 0.00034% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 31% or Less 0.62% or Less 0.023% or Less 0.00034% or Less System Configuration Enforcement System What percentage of the organization's hardware assets are not configured to require local logging on the asset? What percentage of the organization's hardware assets are not configured to require local logging to include detailed information such as a event source, date, timestamp, source addresses, destination addresses, and other useful elements on the asset? What percentage of the organization's hardware assets do not have adequate storage space for the logs generated? What percentage of the organization's hardware assets are not configured to aggregate appropriate logs to a central log management system for analysis and review? What percentage of the organization's hardware assets are not configured to aggregate appropriate logs to a Security Information and Event Management (SIEM) or log analytic tools for log correlation and analysis? What percentage of the organization's hardware assets have not had their logs reviewed recently to identify anomalies or abnormal events? What percentage of the organization's SIEM systems have not recently been tuned to better identify actionable events and decrease event noise? What percentage of the organization's hardware assets are running unsupported web browsers and email client software? What percentage of the organization's hardware assets are utilizing unauthorized browser or email client plugins or add-on applications? What percentage of the organization's hardware assets are utilizing unauthorized scripting languages that run in all web browsers and email clients? 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less Network URL Filtering System What percentage of the organization's hardware assets (whether physically at an organization's facilities or not) are not required to utilize network-based URL filters? 69% or Less Network URL Filtering System Has the organization subscribed to URL categorization services to ensure that they are up-to-date with the most recent website category definitions available? No Log Management System / SIEM What percentage of the organization's hardware assets (whether physically at an organization's facilities or not) are not required to log all URL requests made from the organization's system? 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less What percentage of the organization's DNS servers are using DNS filtering to help block access to known malicious domains? Has the organization implemented Domain-based Message Authentication, Reporting and Conformance (DMARC), starting by implementing the Sender Policy Framework (SPF) and the DomainKeys Identified Mail(DKIM) standards? Has the organization blocked all e-mail attachments entering the organization's e-mail gateway if the file types are unnecessary for the organization's business? Does the organization utilize sandboxing to analyze and block inbound email attachments with malicious behavior? What percentage of the organization's hardware assets do not utilize centrally managed anti-malware software to continuously monitor and defend each of the organization's workstations and servers? What percentage of the organization's hardware assets do not utilize recently updated, centrally managed antimalware software to continuously monitor and defend each of the organization's workstations and servers? What percentage of the organization's hardware assets are not configured to require anti-exploitation features such as Data Execution Prevention (DEP) or Address Space Layout Randomization (ASLR) that are available in an operating system or deploy appropriate toolkits that can be configured to apply protection to a broader set of applications and executables? What percentage of the organization's hardware assets are not configured so that they automatically conduct an anti-malware scan of removable media when inserted or connected? What percentage of the organization's hardware assets are not configured to not auto-run content from removable media? What percentage of the organization's hardware assets do not utilize centrally managed anti-malware software to continuously monitor and defend each of the organization's workstations and servers? What percentage of the organization's Domain Name System (DNS) servers are not configured to require query logging to detect hostname lookups for known malicious domains? What percentage of the organization's hardware assets have not enabled command-line audit logging for command shells, such as Python or Windows PowerShell with enhanced logging enabled? What percentage of the organization's hardware assets do not associate active ports, services and protocols to the hardware assets in the asset inventory? What percentage of the organization's hardware assets are not configured to require that only network ports, protocols, and services listening on a system with validated business needs, are running on each system? What percentage of the organization's hardware assets are not regularly scanned by a port scanner to alert if unauthorized ports are detected on a system? What percentage of the organization's hardware assets are not utilizing host-based firewalls or port filtering tools on end systems, with a default-deny rule that drops all traffic except those services and ports that are explicitly allowed? What percentage of the organization's critical servers are not required to utilize application layer firewalls to verify and validate the traffic going to the server? What percentage of the organization's hardware assets are not configured to back up system data automatically on a regular basis? What percentage of the organization's hardware assets are not configured to back up the complete asset automatically on a regular basis? What percentage of the organization's hardware asset backups have not been tested recently to ensure that the backup is working properly? What percentage of the organization's hardware asset backups are not properly protected via physical security or encryption when they are stored, as well as when they are moved across the network (this includes remote backups and cloud services as well)? What percentage of the organization's hardware assets does not have at least one backup destination that is not continuously addressable through operating system calls? What percentage of the organization's network devices do not utilize a standard, documented security configuration standard for the device? What percentage of the organization's network devices do not have all configuration rules that allow traffic to flow through network devices be documented in a configuration management system with a specific business reason for each rule, a specific individual’s name responsible for that business need, and an expected duration of the need? What percentage of the organization's network devices are not regularly compared against approved security configurations defined for each network device in use and alert when any deviations are discovered? What percentage of the organization's network devices are not utilizing the latest stable version of any securityrelated updates? What percentage of the organization's network devices are not managed using multi-factor authentication and encrypted sessions? 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less DNS Domain Filtering System Anti-Spam Gateway Anti-Spam Gateway Anti-Spam Gateway Endpoint Protection System Endpoint Protection System System Configuration Enforcement System Endpoint Protection System System Configuration Enforcement System Endpoint Protection System DNS Domain Filtering System Log Management System / SIEM SCAP Based Vulnerability Management System SCAP Based Vulnerability Management System SCAP Based Vulnerability Management System 10.1 Ensure Regular Automated Back Ups Ensure that all system data is automatically backed up on regular basis. Backup / Recovery System 10.2 Perform Complete System Backups 10.3 Test Data on Backup Media 10.4 Ensure Protection of Backups 11.5 0.62% or Less 0.00034% or Less Application Aware Firewall 11.4 0.00034% or Less 0.00034% or Less 0.023% or Less Place application firewalls in front of any critical servers to verify and validate the traffic going to the server. Any unauthorized traffic should be blocked and logged. 11.3 0.023% or Less 0.023% or Less 0.62% or Less Implement Application Firewalls Use Automated Tools to Verify Standard Device Configurations and Detect Changes Install the Latest Stable Version of Any Securityrelated Updates on All Network Devices Manage Network Devices Using Multi-Factor Authentication and Encrypted Sessions 0.62% or Less 0.62% or Less 6.7% or Less 9.5 Document Traffic Configuration Rules 0.00034% or Less Yes No 6.7% or Less Network Time Protocol (NTP) Systems Apply host-based firewalls or port filtering tools on end systems, with a default-deny rule that drops all traffic except those services and ports that are explicitly allowed. 11.2 0.023% or Less 31% or Less SCAP Based Vulnerability Management System Apply Host-based Firewalls or Port Filtering 11.1 0.62% or Less 69% or Less System Configuration Enforcement System 9.4 Ensure Backups Have At least One NonContinuously Addressable Destination Maintain Standard Security Configurations for Network Devices 6.7% or Less 0.00034% or Less System Configuration Baselines & Images Perform Regular Automated Port Scans 10.5 31% or Less 0.023% or Less System Configuration Baselines & Images 9.3 Ensure that each of the organization's key systems are backed up as a complete system, through processes such as imaging, to enable the quick recovery of an entire system. Test data integrity on backup media on a regular basis by performing a data restoration process to ensure that the backup is properly working. 0.00034% or Less 69% or Less 0.62% or Less Software Whitelisting System Associate active ports, services and protocols to the hardware assets in the asset inventory. 0.023% or Less 6.7% or Less Software Whitelisting System 9.1 0.62% or Less 31% or Less Uninstall or disable any unauthorized browser or email client plugins or add-on applications. Enable command-line audit logging for command shells, such as Microsoft Powershell and Bash. 6.7% or Less 69% or Less Log Management System / SIEM Associate Active Ports, Services and Protocols to Asset Inventory Ensure Only Approved Ports, Protocols and Services Are Running 31% or Less 0.00034% or Less Ensure that only fully supported web browsers and email clients are allowed to execute in the organization, ideally only using the latest version of the browsers and email clients provided by the vendor. Enable Command-line Audit Logging 0.00034% or Less 69% or Less 0.023% or Less On a regular basis, tune your SIEM system to better identify actionable events and decrease event noise. 8.8 0.023% or Less 0.62% or Less Ensure Use of Only Fully Supported Browsers and Email Clients Disable Unnecessary or Unauthorized Browser or Email Client Plugins Limit Use of Scripting Languages in Web Browsers and Email Clients Enable Domain Name System (DNS) query logging to detect hostname lookups for known malicious domains. 0.62% or Less 31% or Less Regularly Tune SIEM Send all malware detection events to enterprise anti-malware administration tools and event log servers for analysis and alerting. 6.7% or Less 69% or Less 6.8 Enable DNS Query Logging 0.00034% or Less 31% or Less 0.00034% or Less Log Management System / SIEM Centralize Anti-malware Logging 6.7% or Less 69% or Less 0.023% or Less Log Management System / SIEM 8.7 0.00034% or Less 0.023% or Less 6.7% or Less 0.62% or Less On a regular basis, review logs to identify anomalies or abnormal events. 8.6 0.023% or Less 0.62% or Less 6.7% or Less 6.7% or Less Deploy Security Information and Event Management (SIEM) or log analytic tool for log correlation and analysis. Configure devices to not auto-run content from removable media. 0.62% or Less 31% or Less 6.7% or Less 31% or Less Regularly Review Logs Configure Devices Not To Auto-run Content 6.7% or Less 69% or Less 6.7% or Less 69% or Less Deploy SIEM or Log Analytic tool 8.5 Has the organization utilized a risk-rating process to prioritize the remediation of discovered vulnerabilities? 31% or Less 6.7% or Less 0.00034% or Less 6.7 Configure devices so that they automatically conduct an anti-malware scan of removable media when inserted or connected. What percentage of the organization's identified vulnerabilities have not been remediated in a timely manner? 69% or Less 6.7% or Less 0.023% or Less 6.6 Configure Anti-Malware Scanning of Removable Devices 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 0.023% or Less Log Management System / SIEM 8.4 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less Yes No 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 0.62% or Less Ensure that appropriate logs are being aggregated to a central log management system for analysis and review. Enable anti-exploitation features such as Data Execution Prevention (DEP) or Address Space Layout Randomization (ASLR) that are available in an operating system or deploy appropriate toolkits that can be configured to apply protection to a broader set of applications and executables. 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less What percentage of the organization unauthorized software are either removed or the inventory is updated in a timely manner? What percentage of the organization's hardware assets are not utilizing application whitelisting technology to block unauthorized applications from executing on the system? What percentage of the organization's hardware assets are not utilizing application whitelisting technology to block unauthorized applications at the library level from executing on the system? What percentage of the organization's hardware assets are not utilizing application whitelisting technology to block unauthorized scripts from executing on the system? What percentage of high risk business applications have not been physically or logically segregated from other business systems? What percentage of the organization's hardware assets have not recently been scanned by an SCAP compliant configuration monitoring system to identify all potential vulnerabilities on the organization's systems? What percentage of the organization's hardware assets have not recently been scanned by an SCAP compliant configuration monitoring system to identify all potential vulnerabilities on the organization's systems utilizing an authenticated connection to the system? What percentage of the organization's hardware assets have not recently been scanned by an SCAP compliant configuration monitoring system to identify all potential vulnerabilities on the organization's systems utilizing a dedicated service account and host-based restrictions? What percentage of the organization's hardware assets are not regularly updated by an automated software update tools in order to ensure that the operating systems are running the most recent security updates provided by the software vendor? What percentage of the organization's hardware assets are not regularly updated by an automated software update tools in order to ensure that third-party software is running the most recent security updates provided by the software vendor? 0.62% or Less Central Log Management Enable Operating System Anti-Exploitation Features/ Deploy Anti-Exploit Technologies 0.00034% or Less 0.00034% or Less 6.7% or Less 6.7% or Less 6.5 8.3 0.00034% or Less 0.023% or Less 0.023% or Less 6.7% or Less 6.7% or Less Log Management System / SIEM 8.2 0.023% or Less 0.62% or Less 0.62% or Less 6.7% or Less 31% or Less Ensure that all systems that store logs have adequate storage space for the logs generated. Ensure Anti-Malware Software and Signatures are Updated 0.62% or Less 31% or Less 31% or Less 69% or Less Ensure adequate storage for logs Utilize Centrally Managed Anti-malware Software 31% or Less 69% or Less 69% or Less What percentage of the organization's master images are not stored on securely configured servers, validated with integrity checking tools, to ensure that only authorized changes to the images are possible? What percentage of the organization's hardware assets are not automatically configured via system configuration management tools that automatically enforce and redeploy configuration settings to systems at regularly scheduled intervals? What percentage of the organization's hardware assets have not recently been scanned by an SCAP compliant configuration monitoring system to verify all security configuration elements, and alert when unauthorized changes occur? What percentage of the organization's hardware assets do not utilize at least three synchronized time sources from which all servers and network devices retrieve time information on a regular basis so that timestamps in logs are consistent? 6.4 8.1 69% or Less What percentage of the organization's hardware assets have not recently been scanned by a software inventory tool to document the software installed on the system? What percentage of software assets are not documented in a software inventory system that tracks the name, version, publisher, and install date for all software, including operating systems authorized by the organization? 31% or Less Log Management System / SIEM Utilize centrally managed anti-malware software to continuously monitor and defend each of the organization's workstations and servers. Ensure that the organization's anti-malware software updates its scanning engine and signature database on a regular basis. What percentage of the organization's software applications or operating systems are not currently supported by the software's vendor? 69% or Less Enable system logging to include detailed information such as a event source, date, user, timestamp, source addresses, destination addresses, and other useful elements. Use sandboxing to analyze and block inbound email attachments with malicious behavior. 0.00034% or Less 0.00034% or Less 6.7% or Less What percentage of the organization's hardware assets are not based upon secure images or templates based on the organization's approved configuration standards? Enable Detailed Logging Sandbox All Email Attachments 0.023% or Less 0.023% or Less 31% or Less 31% or Less 31% or Less 31% or Less 6.3 Block Unnecessary File Types 0.62% or Less 0.62% or Less 31% or Less Log Management System / SIEM 7.9 31% or Less 31% or Less 69% or Less 69% or Less 69% or Less 69% or Less Ensure that local logging has been enabled on all systems and networking devices. 7.10 69% or Less 69% or Less 69% or Less Activate audit logging To lower the chance of spoofed or modified emails from valid domains, implement Domain-based Message Authentication, Reporting and Conformance (DMARC) policy and verification, starting by implementing the Sender Policy Framework (SPF) and the DomainKeys Identified Mail(DKIM) standards. Block all e-mail attachments entering the organization's e-mail gateway if the file types are unnecessary for the organization's business. 0.00034% or Less What percentage of the organization's network switches are not configured to require network-based port level access control utilizing client certificates to authenticate all client connections? What percentage of the organization's software are not presently included in the organization's software inventory? Software Whitelisting System Utilize Three Synchronized Time Sources Implement DMARC and Enable Receiver-Side Verification 0.023% or Less What percentage of the organization's systems limit access to scripting tools (such as Microsoft PowerShell and Python) to only administrative or development users with the need to access those capabilities? What percentage of the organizations hardware assets are not configured to issue a log entry and alert when an Log Management System / SIEM account is added to or removed from any group assigned elevated privileges? What percentage of the organization's hardware assets are not configured to issue a log entry and alert on Log Management System / SIEM unsuccessful logins to an administrative account? What percentage of the organization's authorized operating systems and software does not have a documented, System Configuration Baselines & Images standard security configuration? Dedicated Administration Systems 6.2 7.8 0.62% or Less What percentage of the organization's system administrators are not required to use a dedicated machine for all administrative tasks or tasks requiring elevated access? Multi-Factor Authentication System 6.1 Use DNS filtering services to help block access to known malicious domains. 6.7% or Less 31% or Less 31% or Less Use at least three synchronized time sources from which all servers and network devices retrieve time information on a regular basis so that timestamps in logs are consistent. Use of DNS Filtering Services 31% or Less 31% or Less 5.5 Log all URL requests 69% or Less 69% or Less 69% or Less Utilize a Security Content Automation Protocol (SCAP) compliant configuration monitoring system to verify all security configuration elements, catalog approved exceptions, and alert when unauthorized changes occur. 7.7 0.00034% or Less What percentage of the organization's network switches are not configured to require network-based port level access control for all client connections? 69% or Less Implement Automated Configuration Monitoring Systems 7.6 0.023% or Less What percentage of the organization's systems, where multi-factor authentication is not supported (such as local administrator, root, or service accounts), accounts will use passwords that are unique to that system? What percentage of the organization's hardware assets are not configured to utilize multi-factor authentication and encrypted channels for all elevated account access? Deploy system configuration management tools that will automatically enforce and redeploy configuration settings to systems at regularly scheduled intervals. Subscribe to URL-Categorization service 0.62% or Less What percentage of the organization's user accounts with elevated rights do not utilize a dedicated or secondary account for elevated activities? Privileged Account Management System Deploy System Configuration Management Tools 7.5 6.7% or Less Privileged Account Management System 5.4 Enforce network-based URL filters that limit a system's ability to connect to websites not approved by the organization. This filtering shall be enforced for each of the organization's systems, whether they are physically at an organization's facilities or not. Subscribe to URL categorization services to ensure that they are up-to-date with the most recent website category definitions available. Uncategorized sites shall be blocked by default. Log all URL requests from each of the organization's systems, whether onsite or a mobile device, in order to identify potentially malicious activity and assist incident handlers with identifying potentially compromised systems. 31% or Less 6.7% or Less Sigma Level Six 0.00034% or Less 0.00034% or Less 0.00034% or Less 31% or Less 31% or Less Securely Store Master Images Maintain and Enforce Network-Based URL Filters 0.00034% or Less 69% or Less Is the organization's software inventory system tied into the hardware asset inventory system? Sigma Level Sigma Sigma Three Level Four Level Five 0.62% or 0.023% or 6.7% or Less Less Less 0.62% or 0.023% or 6.7% or Less Less Less 0.62% or 0.023% or 6.7% or Less Less Less 69% or Less 69% or Less 5.3 7.4 0.00034% or Less 0.023% or Less What percentage of the organization's systems utilize default passwords for accounts with elevated capabilities? Maintain Secure Images Ensure that only authorized scripting languages are able to run in all web browsers and email clients. 0.023% or Less 0.62% or Less What percentage of the organization's hardware assets have not recently utilized automated tools to inventory all administrative accounts to ensure that only authorized individuals have elevated privileges? 5.2 7.3 0.62% or Less 6.7% or Less What percentage of the organization's hardware assets as a whole are not documented in the organization's asset inventory with the appropriate network address, hardware address, machine name, data asset owner, and department for each asset? What percentage of the organization's unauthorized assets have not been removed from the network, quarantined or added to the inventory in a timely manner? Privileged Account Management System Establish Secure Configurations 7.2 6.7% or Less 31% or Less What percentage of the organization's hardware assets are not presently included in the organization's asset inventory? Privileged Account Management System 5.1 7.1 31% or Less 69% or Less What percentage of the organization's DHCP servers do not have logging enabled? Asset Inventory System Run Automated Vulnerability Scanning Tools Use Multifactor Authentication For All Administrative Use multi-factor authentication and encrypted channels for all administrative account access. Access Ensure administrators use a dedicated machine for all administrative tasks or tasks requiring administrative Use of Dedicated Machines For All Administrative access. This machine will be segmented from the organization's primary network and not be allowed Internet Tasks access. This machine will not be used for reading e-mail, composing documents, or browsing the Internet. Limit access to scripting tools (such as Microsoft PowerShell and Python) to only administrative or development Limit Access to Script Tools users with the need to access those capabilities. Log and Alert on Changes to Administrative Group Configure systems to issue a log entry and alert when an account is added to or removed from any group Membership assigned administrative privileges. Log and Alert on Unsuccessful Administrative Configure systems to issue a log entry and alert on unsuccessful logins to an administrative account. Account Login 69% or Less What percentage of the organization's networks are not being monitored by a passive asset discovery tool? Log Management System / SIEM 3.1 4.5 Sigma Level Two 31% or Less 31% or Less 31% or Less Passive Device Discovery System Utilize application whitelisting technology on all assets to ensure that only authorized software executes and all Software Whitelisting System unauthorized software is blocked from executing on assets. The organization's application whitelisting software must ensure that only authorized software libraries (such as Software Whitelisting System *.dll, *.ocx, *.so, etc) are allowed to load into a system process. The organization's application whitelisting software must ensure that only authorized, digitally signed scripts Software Whitelisting System (such as *.ps1, *.py, macros, etc) are allowed to run on a system. Physically or logically segregated systems should be used to isolate and run software that is required for Network Firewall / Access Control System business operations but incur higher risk for the organization. Utilize an up-to-date SCAP-compliant vulnerability scanning tool to automatically scan all systems on the network SCAP Based Vulnerability Management on a weekly or more frequent basis to identify all potential vulnerabilities on the organization's systems. System Use automated tools to inventory all administrative accounts, including domain and local accounts, to ensure that only authorized individuals have elevated privileges. Before deploying any new asset, change all default passwords to have values consistent with administrative level accounts. Ensure that all users with administrative account access use a dedicated or secondary account for elevated activities. This account should only be used for administrative activities and not internet browsing, email, or similar activities. Where multi-factor authentication is not supported (such as local administrator, root, or service accounts), accounts will use passwords that are unique to that system. Sigma Level One 69% or Less 69% or Less 69% or Less Measure What percentage of the organization's networks have not recently been scanned by an active asset discovery tool? Host Based Firewall Backup / Recovery System Backup / Recovery System Ensure that backups are properly protected via physical security or encryption when they are stored, as well as when they are moved across the network. This includes remote backups and cloud services. Backup / Recovery System Ensure that all backups have at least one backup destination that is not continuously addressable through operating system calls. Backup / Recovery System Maintain standard, documented security configuration standards for all authorized network devices. Network Device Management System All configuration rules that allow traffic to flow through network devices should be documented in a configuration management system with a specific business reason for each rule, a specific individual’s name responsible for that business need, and an expected duration of the need. Network Device Management System Compare all network device configuration against approved security configurations defined for each network device in use and alert when any deviations are discovered. Network Device Management System Install the latest stable version of any security-related updates on all network devices. Network Device Management System Manage all network devices using multi-factor authentication and encrypted sessions. Multi-Factor Authentication System 6.7% or Less Yes Yes No Yes No Yes No 69% or Less 69% or Less 31% or Less 31% or Less 69% or Less 31% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 69% or Less 31% or Less 69% or Less 69% or Less 69% or Less 69% or Less 31% or Less 31% or Less 31% or Less 31% or Less 69% or Less 31% or Less 69% or Less 69% or Less 31% or Less 31% or Less 69% or Less 31% or Less 69% or Less 69% or Less 69% or Less 31% or Less 31% or Less 31% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less CIS Controls Measures and Metrics for Version 7 Sub--Control 11.6 11.7 12.1 12.2 12.3 12.4 12.5 12.6 12.7 12.8 12.9 12.10 12.11 12.12 13.1 13.2 13.3 13.4 13.5 Title Description Encrypt the Hard Drive of All Mobile Devices. 13.7 Manage USB Devices 13.8 Manage System's External Removable Media's Read/write Configurations If USB storage devices are required, enterprise software should be used that can configure systems to allow the use of specific devices. An inventory of such devices should be maintained. Configure systems not to write data to external removable media, if there is no business need for supporting such devices. 13.9 Encrypt Data on USB Storage Devices If USB storage devices are required, all data stored on such devices must be encrypted while at rest. 14.2 14.3 14.4 14.5 14.6 14.7 14.8 14.9 15.1 15.2 15.3 15.4 15.5 15.6 15.7 Measure What percentage of the organization's network engineers are not utilizing a dedicated machine for all administrative tasks or tasks requiring elevated access to the organization's network devices? What percentage of the organization's network engineers are not utilizing a dedicated machine, located on a dedicated management network, for all administrative tasks or tasks requiring elevated access to the organization's network devices? Does the organization maintain an up-to-date inventory of all of the organization's network boundaries? What percentage of the organization's hardware assets have not recently been scanned to identify unauthorized network boundaries? Are each of the organization's network boundaries configured to deny communications with known malicious or unused Internet IP addresses and limit access only to trusted and necessary IP address ranges? Are each of the organization's network boundaries configured to deny communication over unauthorized TCP or UDP ports or application traffic to ensure that only authorized protocols are allowed to cross the network boundary in or out of the network? What percentage of the organization's network boundaries are not configured to record network packets passing through the boundary? What percentage of the organization's network boundaries are not configured to require network-based Intrusion Deploy network-based Intrusion Detection Systems (IDS) sensors to look for unusual attack mechanisms and Network Based Intrusion Detection System Deploy Network-based IDS Sensor Detection Systems (IDS) sensors to look for unusual attack mechanisms and detect compromise of these detect compromise of these systems at each of the organization's network boundaries. (NIDS) systems the boundary? What percentage of the organization's organization's network boundaries are not configured to require networkDeploy Network-Based Intrusion Prevention Deploy network-based Intrusion Prevention Systems (IPS) to block malicious network traffic at each of the Network Based Intrusion Prevention based Intrusion Prevention Systems (IPS) sensors to look for unusual attack mechanisms and detect Systems organization's network boundaries. System (IPS) compromise of these systems the boundary? Deploy NetFlow Collection on Networking Boundary What percentage of the organization's network boundary devices are not required to use NetFlow and logging Enable the collection of NetFlow and logging data on all network boundary devices. Network Device Management System Devices data on the devices? Ensure that all network traffic to or from the Internet passes through an authenticated application layer proxy that What percentage of the organization's network boundaries are not configured to pass through an authenticated Deploy Application Layer Filtering Proxy Server Network Firewall / Access Control System is configured to filter unauthorized connections. application layer proxy that is configured to filter unauthorized connections? Decrypt all encrypted network traffic at the boundary proxy prior to analyzing the content. However, the What percentage of the organization's network boundaries are not configured to decrypt all encrypted network Decrypt Network Traffic at Proxy organization may use whitelists of allowed sites that can be accessed through the proxy without decrypting the Network Firewall / Access Control System traffic prior to analyzing the content? traffic. Require All Remote Login to Use Multi-factor Require all remote login access to the organization's network to encrypt data in transit and use multi-factor What percentage of the organization's hardware devices are not required to utilize encryption and multi-factor Multi-Factor Authentication System Authentication authentication. authentication when remotely accessing the organization's network systems? Scan all enterprise devices remotely logging into the organization's network prior to accessing the network to What percentage of the organization's devices remotely logging into the organization's network are not scanned Manage All Devices Remotely Logging into Internal System Configuration Enforcement ensure that each of the organization's security policies has been enforced in the same manner as local network prior to accessing the network to ensure that each of the organization's security policies has been enforced in the Network System devices. same manner as local network devices? Maintain an inventory of all sensitive information stored, processed, or transmitted by the organization's Does the organization maintain an inventory of all sensitive information stored, processed, or transmitted by the Maintain an Inventory Sensitive Information Data Inventory / Classification System technology systems, including those located onsite or at a remote service provider. organization's technology systems, including those located onsite or at a remote service provider? Remove sensitive data or systems not regularly accessed by the organization from the network. These systems Remove Sensitive Data or Systems Not Regularly Does the organization regularly remove sensitive data sets or systems not regularly accessed by the shall only be used as stand alone systems (disconnected from the network) by the business unit needing to Data Inventory / Classification System Accessed by Organization organization from the network? occasionally use the system or completely virtualized and powered off until needed. Deploy an automated tool on network perimeters that monitors for unauthorized transfer of sensitive information Network Based Data Loss Prevention Has the organization deployed an automated tool on network perimeters that monitors for sensitive information Monitor and Block Unauthorized Network Traffic and blocks such transfers while alerting information security professionals. (DLP) System and blocks such transfers while alerting information security professionals? Only Allow Access to Authorized Cloud Storage or Only allow access to authorized cloud storage or email providers. Network Firewall / Access Control System Does the organization only allow access to authorized cloud storage or email providers? Email Providers Monitor and Detect Any Unauthorized Use of Network Based Data Loss Prevention What percentage of the organization's network boundaries are not configured to monitor all traffic leaving the Monitor all traffic leaving the organization and detect any unauthorized use of encryption. Encryption (DLP) System organization and detect any unauthorized use of encryption? 13.6 14.1 Sensor Ensure network engineers use a dedicated machine for all administrative tasks or tasks requiring elevated Use Dedicated Machines For All Network access. This machine shall be segmented from the organization's primary network and not be allowed Internet Dedicated Administration Systems Administrative Tasks access. This machine shall not be used for reading e-mail, composing documents, or surfing the Internet. Manage the network infrastructure across network connections that are separated from the business use of that Manage Network Infrastructure Through a network, relying on separate VLANs or, preferably, on entirely different physical connectivity for management Dedicated Administration Systems Dedicated Network sessions for network devices. Maintain an Inventory of Network Boundaries Maintain an up-to-date inventory of all of the organization's network boundaries. Network Firewall / Access Control System Scan for Unauthorized Connections across Trusted Perform regular scans from outside each trusted network boundary to detect any unauthorized connections System Configuration Enforcement Network Boundaries which are accessible across the boundary. System Deny Communications with Known Malicious IP Deny communications with known malicious or unused Internet IP addresses and limit access only to trusted and Network Firewall / Access Control System Addresses necessary IP address ranges at each of the organization's network boundaries,. Deny communication over unauthorized TCP or UDP ports or application traffic to ensure that only authorized Deny Communication over Unauthorized Ports protocols are allowed to cross the network boundary in or out of the network at each of the organization's Network Firewall / Access Control System network boundaries. Configure Monitoring Systems to Record Network Configure monitoring systems to record network packets passing through the boundary at each of the Network Packet Capture System Packets organization's network boundaries. Utilize approved whole disk encryption software to encrypt the hard drive of all mobile devices. Segment the network based on the label or classification level of the information stored on the servers, locate all Segment the Network Based on Sensitivity sensitive information on separated Virtual Local Area Networks (VLANs). Enable firewall filtering between VLANs to ensure that only authorized systems are able to communicate with Enable Firewall Filtering Between VLANs other systems necessary to fulfill their specific responsibilities. Disable all workstation to workstation communication to limit an attacker's ability to move laterally and Disable Workstation to Workstation Communication compromise neighboring systems, through technologies such as Private VLANs or microsegmentation. Encrypt All Sensitive Information in Transit Encrypt all sensitive information in transit. Utilize an active discovery tool to identify all sensitive information stored, processed, or transmitted by the Utilize an Active Discovery Tool to Identify Sensitive organization's technology systems, including those located onsite or at a remote service provider and update the Data organization's sensitive information inventory. Protect all information stored on systems with file system, network share, claims, application, or database Protect Information through Access Control Lists specific access control lists. These controls will enforce the principle that only authorized individuals should have access to the information based on their need to access the information as a part of their responsibilities. Enforce Access Control to Data through Automated Use an automated tool, such as host-based Data Loss Prevention, to enforce access controls to data even when Tools data is copied off a system. Encrypt all sensitive information at rest using a tool that requires a secondary authentication mechanism not Encrypt Sensitive Information at Rest integrated into the operating system, in order to access the information. Enforce Detail Logging for Access or Changes to Enforce detailed audit logging for access to sensitive data or changes to sensitive data (utilizing tools such as Sensitive Data File Integrity Monitoring or Security Information and Event Monitoring). Maintain an Inventory of Authorized Wireless Maintain an inventory of authorized wireless access points connected to the wired network. Access Points Detect Wireless Access Points Connected to the Configure network vulnerability scanning tools to detect and alert on unauthorized wireless access points Wired Network connected to the wired network. Use a wireless intrusion detection system (WIDS) to detect and alert on unauthorized wireless access points Use a Wireless Intrusion Detection System connected to the network. Disable Wireless Access on Devices if Not Required Disable wireless access on devices that do not have a business purpose for wireless access. Limit Wireless Access on Client Devices Configure wireless access on client machines that do have an essential wireless business purpose, to allow access only to authorized wireless networks and to restrict access to other wireless networks. Disable Peer-to-peer Wireless Network Capabilities Disable peer-to-peer (adhoc) wireless network capabilities on wireless clients. on Wireless Clients Leverage the Advanced Encryption Standard (AES) Leverage the Advanced Encryption Standard (AES) to encrypt wireless data in transit. to Encrypt Wireless Data 15.8 Use Wireless Authentication Protocols that Require Ensure that wireless networks use authentication protocols such as Extensible Authentication Protocol-Transport Mutual, Multi-Factor Authentication Layer Security (EAP/TLS), that requires mutual, multi-factor authentication. 15.9 Disable Wireless Peripheral Access of Devices Whole Disk Encryption System What percentage of the organization's mobile devices do not utilize approved whole disk encryption software? What percentage of the organization's hardware assets are not configured to only allow the use of specific USB devices? What percentage of the organization's hardware assets are not configured not to write data to USB storage devices, if there is no business need for supporting such devices? What percentage of the organization's hardware assets are not configured to encrypt all data stored on USB Endpoint Protection System devices? What percentage of the organization's network devices are not located on dedicated Virtual Local Area Networks Network Firewall / Access Control System (VLANs)? What percentage of the organization's network devices are not located on dedicated Virtual Local Area Networks Network Firewall / Access Control System (VLANs) separated by firewall filters? What percentage of the organization's workstation devices are not located on dedicated Private Virtual Local Network Firewall / Access Control System Area Networks (PVLANs)? System Configuration Enforcement What percentage of the organization's sensitive information is not encrypted in transit? System Endpoint Protection System Endpoint Protection System Sigma Level One Sigma Level Two 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less No 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 69% or Less 69% or Less 31% or Less 31% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less No Yes No Yes 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less What percentage of the organizations systems do not use an automated tool, such as host-based Data Loss Prevention, to enforce access controls to data even when data is copied off a system? What percentage of the organization's sensitive information is not encrypted at rest and requires a secondary authentication mechanism not integrated into the operating system, in order to access the information? What percentage of the organization's sensitive information does not require detailed audit logging when the data is accessed? What percentage of the organization's wireless access points have not been authorized in the organization's wireless access point inventory? What percentage of the organization's hardware assets have not recently been scanned to detect and alert on unauthorized wireless access points connected to the wired network? What percentage of the organization's facilities do not have a wireless intrusion detection system (WIDS) to detect and alert on unauthorized wireless access points connected to the network? What percentage of the organization's hardware assets is not configured to disable wireless access in devices that do not have a business purpose for wireless access? What percentage of the organization's hardware assets are not configured to allow access only to authorized wireless networks and to restrict access for other wireless networks? What percentage of the organization's hardware assets are not configured to disable peer-to-peer (adhoc) wireless network capabilities on wireless clients? What percentage of the organization's hardware assets are not configured to leverage the Advanced Encryption Standard (AES) to encrypt wireless data in transit? What percentage of the organization's hardware assets are not configured to utilize wireless networks to use authentication protocols such as Extensible Authentication Protocol-Transport Layer Security (EAP/TLS), that requires mutual, multi-factor authentication? What percentage of the organization's hardware assets are not configured to disable wireless peripheral access of devices (such as Bluetooth), unless such access is required for a business purpose? 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 69% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 31% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less 0.023% or Less 0.00034% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.023% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.00034% or Less 0.62% or Less Yes 0.023% or Less 0.00034% or Less 0.62% or Less Yes 0.023% or Less 0.00034% or Less Host Based Data Loss Prevention (DLP) System Host Based Data Loss Prevention (DLP) System Log Management System / SIEM Network Device Management System SCAP Based Vulnerability Management System Wireless Intrusion Detection System (WIDS) System Configuration Enforcement System System Configuration Enforcement System System Configuration Enforcement System Network Device Management System Network Device Management System Identity & Access Management System Identity & Access Management System What percentage of the organization's accounts are not included in the organization's inventory? 16.7 Establish Process for Revoking Access Establish and follow an automated process for revoking system access by disabling accounts immediately upon termination or change of responsibilities of an employee or contractor . Disabling these accounts, instead of deleting accounts, allows preservation of audit trails. Identity & Access Management System Has the organization established and followed an automated process for revoking system access by disabling accounts immediately upon termination or change of responsibilities of an employee or contractor? 16.8 Disable Any Unassociated Accounts Disable any account that cannot be associated with a business process or business owner. Identity & Access Management System 16.9 Disable Dormant Accounts Automatically disable dormant accounts after a set period of inactivity. Identity & Access Management System System Configuration Enforcement System Network Device Management System Multi-Factor Authentication System 16.10 Ensure All Accounts Have An Expiration Date Ensure that all accounts have an expiration date that is monitored and enforced. Identity & Access Management System 16.11 Lock Workstation Sessions After Inactivity Automatically lock workstation sessions after a standard period of inactivity. Identity & Access Management System 16.12 Monitor Attempts to Access Deactivated Accounts Monitor attempts to access deactivated accounts through audit logging. 16.13 Alert on Account Login Behavior Deviation Alert when users deviate from normal login behavior, such as time-of-day, workstation location and duration. Log Management System / SIEM 17.1 Perform a Skills Gap Analysis Perform a skills gap analysis to understand the skills and behaviors workforce members are not adhering to, using this information to build a baseline education roadmap. Training / Awareness Education Plans 17.2 Deliver Training to Fill the Skills Gap Deliver training to address the skills gap identified to positively impact workforce members' security behavior. Training / Awareness Education Plans 17.3 Implement a Security Awareness Program Create a security awareness program for all workforce members to complete on a regular basis to ensure they understand and exhibit the necessary behaviors and skills to help ensure the security of the organization. The organization's security awareness program should be communicated in a continuous and engaging manner. Training / Awareness Education Plans 17.4 Update Awareness Content Frequently Ensure that the organization's security awareness program is updated frequently (at least annually) to address new technologies, threats, standards and business requirements. Training / Awareness Education Plans 17.5 Train Workforce on Secure Authentication Train workforce members on the importance of enabling and utilizing secure authentication. Training / Awareness Education Plans 17.6 Train Workforce on Identifying Social Engineering Attacks Train the workforce on how to identify different forms of social engineering attacks, such as phishing, phone scams and impersonation calls. Training / Awareness Education Plans 17.7 Train Workforce on Sensitive Data Handling Train workforce on how to identify and properly store, transfer, archive and destroy sensitive information. Training / Awareness Education Plans Train Workforce on Causes of Unintentional Data Exposure Train Workforce Members on Identifying and Reporting Incidents Train workforce members to be aware of causes for unintentional data exposures, such as losing their mobile devices or emailing the wrong person due to autocomplete in email. Train employees to be able to identify the most common indicators of an incident and be able to report such an incident. Establish secure coding practices appropriate to the programming language and development environment being used. For in-house developed software, ensure that explicit error checking is performed and documented for all input, including for size, data type, and acceptable ranges or formats. Verify that the version of all software acquired from outside your organization is still supported by the developer or appropriately hardened based on developer security recommendations. 18.5 18.6 18.7 18.8 18.9 18.10 18.11 19.1 19.2 19.3 19.4 19.5 Log Management System / SIEM Training / Awareness Education Plans Training / Awareness Education Plans Secure Coding Standards Secure Coding Standards Secure Coding Standards Only use up-to-date and trusted third-party components for the software developed by the organization. Secure Coding Standards Use only standardized and extensively reviewed encryption algorithms. Secure Coding Standards Ensure that all software development personnel receive training in writing secure code for their specific development environment and responsibilities. Apply static and dynamic analysis tools to verify that secure coding practices are being adhered to for internally Apply Static and Dynamic Code Analysis Tools developed software. Establish a Process to Accept and Address Reports Establish a process to accept and address reports of software vulnerabilities, including providing a means for of Software Vulnerabilities external entities to contact your security group. Maintain separate environments for production and nonproduction systems. Developers should not have Separate Production and Non-Production Systems unmonitored access to production environments. Protect web applications by deploying web application firewalls (WAFs) that inspect all traffic flowing to the web application for common web application attacks. For applications that are not web-based, specific application Deploy Web Application Firewalls (WAFs) firewalls should be deployed if such tools are available for the given application type. If the traffic is encrypted, the device should either sit behind the encryption or be capable of decrypting the traffic prior to analysis. If neither option is appropriate, a host-based web application firewall should be deployed. Use Standard Hardening Configuration Templates For applications that rely on a database, use standard hardening configuration templates. All systems that are for Databases part of critical business processes should also be tested. Ensure that there are written incident response plans that defines roles of personnel as well as phases of Document Incident Response Procedures incident handling/management. Assign job titles and duties for handling computer and network incidents to specific individuals and ensure Assign Job Titles and Duties for Incident Response tracking and documentation throughout the incident through resolution. Designate Management Personnel to Support Designate management personnel, as well as backups, who will support the incident handling process by acting Incident Handling in key decision-making roles. Devise organization-wide standards for the time required for system administrators and other workforce Devise Organization-wide Standards for Reporting members to report anomalous events to the incident handling team, the mechanisms for such reporting, and the Incidents kind of information that should be included in the incident notification. Maintain Contact Information For Reporting Security Assemble and maintain information on third-party contact information to be used to report a security incident, Incidents such as Law Enforcement, relevant government departments, vendors, and ISAC partners. 19.6 Publish Information Regarding Reporting Computer Publish information for all workforce members, regarding reporting computer anomalies and incidents to the Anomalies and Incidents incident handling team. Such information should be included in routine employee awareness activities. 19.7 Conduct Periodic Incident Scenario Sessions for Personnel 19.8 Create Incident Scoring and Prioritization Schema 20.1 Establish a Penetration Testing Program Plan and conduct routine incident response exercises and scenarios for the workforce involved in the incident response to maintain awareness and comfort in responding to real world threats. Exercises should test communication channels, decision making, and incident responders technical capabilities using tools and data available to them. Create incident scoring and prioritization schema based on known or potential impact to your organization. Utilize score to define frequency of status updates and escalation procedures. Establish a program for penetration tests that includes a full scope of blended attacks, such as wireless, clientbased, and web application attacks. 6.7% or Less 6.7% or Less Maintain an inventory of all accounts organized by authentication system. 18.4 6.7% or Less 31% or Less Maintain an Inventory of Accounts Only Use Up-to-date And Trusted Third-Party Components Use Only Standardized and Extensively Reviewed Encryption Algorithms Ensure Software Development Personnel are Trained in Secure Coding 6.7% or Less 69% or Less 16.6 Verify That Acquired Software is Still Supported 6.7% or Less What percentage of the organization's hardware assets have not been configured with appropriate file system, network share, claims, application, or database specific access control lists? 16.5 18.3 6.7% or Less System Configuration Enforcement System Identity & Access Management System 18.2 6.7% or Less 31% or Less Encrypt Transmittal of Username and Authentication Ensure that all account usernames and authentication credentials are transmitted across networks using Credentials encrypted channels. Ensure Explicit Error Checking is Performed for All In-house Developed Software 6.7% or Less 69% or Less Encrypt or Hash all Authentication Credentials Establish Secure Coding Practices 6.7% or Less What percentage of the organization's assets have not been scanned by an active discovery tool to identify all sensitive information stored, processed, or transmitted by the organization's technology systems? 16.4 18.1 6.7% or Less Data Inventory / Classification System No 17.9 Yes No 69% or Less 17.8 6.7% or Less Yes Has the organization configured access for all accounts through as few centralized points of authentication as possible, including network, security, and cloud systems? Encrypt or hash with a salt all authentication credentials when stored. 6.7% or Less No What percentage of the organization's authentication systems are not included in the organization's inventory? 16.3 Yes No Identity & Access Management System 16.2 Yes 69% or Less Identity & Access Management System 16.1 Sigma Level Six Yes No Disable wireless peripheral access of devices (such as Bluetooth and NFC), unless such access is required for a business purpose. Create Separate Wireless Network for Personal and Create a separate wireless network for personal or untrusted devices. Enterprise access from this network Untrusted Devices should be treated as untrusted and filtered and audited accordingly. Maintain an inventory of each of the organization's authentication systems, including those located onsite or at a Maintain an Inventory of Authentication Systems remote service provider. Configure access for all accounts through as few centralized points of authentication as possible, including Configure Centralized Point of Authentication network, security, and cloud systems. Require multi-factor authentication for all user accounts, on all systems, whether managed onsite or by a thirdRequire Multi-factor Authentication party provider. 15.10 Sigma Level Sigma Sigma Three Level Four Level Five Training / Awareness Education Plans Software Vulnerability Scanning Tool Software Vulnerability Scanning Tool Secure Coding Standards Web Application Firewall (WAF) System Configuration Enforcement System Incident Management Plans Incident Management Plans Incident Management Plans Incident Management Plans Incident Management Plans Incident Management Plans Incident Management Plans Incident Management Plans Penetration Testing Plans Does the organization utilize a separate a wireless network for personal or untrusted devices? What percentage of the organization's user accounts do not require multi-factor authentication? What percentage of the organization's hardware assets' authentication files cannot be accessed without root or administrator privileges and are not encrypted or hashed? What percentage of the organization's user accounts and authentication credentials are not transmitted across networks using encrypted channels? What percentage of the organization's user accounts are not disabled if they cannot be associated with a business process or owner? Does the organization automatically disable dormant accounts after a set period of inactivity? What percentage of the organization's user accounts do not have an expiration date that is monitored and enforced? Does the organization automatically lock workstation sessions after a standard period of inactivity? 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less Yes No 69% or Less 69% or Less 69% or Less 69% or Less 31% or Less 6.7% or Less Yes 31% or Less 31% or Less 31% or Less 31% or Less 6.7% or Less 6.7% or Less 6.7% or Less 6.7% or Less 0.62% or Less 0.62% or Less 0.62% or Less 0.62% or Less Yes No 69% or Less No 69% or Less No 0.62% or Less 31% or Less 31% or Less 6.7% or Less 6.7% or Less Does the organization monitor attempts to access deactivated accounts through audit logging? Does the organization alert when users deviate from normal login behavior, such as time-of-day, workstation location and duration? Has the organization performed a skills gap analysis to understand the skills and behaviors workforce members are not adhering to, using this information to build a baseline education roadmap. Has the organization delivered training to address the skills gap identified to positively impact workforce members' security behavior. Has the organization created a security awareness program for all workforce members to complete on a regular basis to ensure they understand and exhibit the necessary behaviors and skills to help ensure the security of the organization. The organization's security awareness program should be communicated in a continuous and engaging manner. Has the organization ensured that the organization's security awareness program is updated frequently (at least annually) to address new technologies, threats, standards and business requirements. Has the organization trained workforce members on the importance of enabling and utilizing secure authentication. Has the organization trained the workforce on how to identify different forms of social engineering attacks, such as phishing, phone scams and impersonation calls. Has the organization trained workforce on how to identify and properly store, transfer, archive and destroy sensitive information. Has the organization trained workforce members to be aware of causes for unintentional data exposures, such as losing their mobile devices or emailing the wrong person due to autocomplete in email. Has the organization trained employees to be able to identify the most common indicators of an incident and be able to report such an incident. Has the organization established secure coding practices appropriate to the programming language and development environment being used. For in-house developed software, has the organization ensured that explicit error checking is performed and documented for all input, including for size, data type, and acceptable ranges or formats. Has the organization verified that the version of all software acquired from outside your organization is still supported by the developer or appropriately hardened based on developer security recommendations. Has the organization only used up-to-date and trusted third-party components for the software developed by the organization. No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes Has the organization used only standardized and extensively reviewed encryption algorithms. No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes Has the organization ensured that all software development personnel receive training in writing secure code for their specific development environment and responsibilities. Has the organization applied static and dynamic analysis tools to verify that secure coding practices are being adhered to for internally developed software. Has the organization established a process to accept and address reports of software vulnerabilities, including providing a means for external entities to contact your security group. Has the organization maintained separate environments for production and nonproduction systems. Developers should not have unmonitored access to production environments. Has the organization protected web applications by deploying web application firewalls (WAFs) that inspect all traffic flowing to the web application for common web application attacks. For applications that are not webbased, specific application firewalls should be deployed if such tools are available for the given application type. If the traffic is encrypted, the device should either sit behind the encryption or be capable of decrypting the traffic prior to analysis. If neither option is appropriate, a host-based web application firewall should be deployed. For applications that rely on a database, has the organization used standard hardening configuration templates. All systems that are part of critical business processes should also be tested. Has the organization ensured that there are written incident response plans that defines roles of personnel as well as phases of incident handling/management. Has the organization assigned job titles and duties for handling computer and network incidents to specific individuals and ensure tracking and documentation throughout the incident through resolution. Has the organization designated management personnel, as well as backups, who will support the incident handling process by acting in key decision-making roles. Has the organization devised organization-wide standards for the time required for system administrators and other workforce members to report anomalous events to the incident handling team, the mechanisms for such reporting, and the kind of information that should be included in the incident notification. Has the organization assembled and maintain information on third-party contact information to be used to report a security incident, such as Law Enforcement, relevant government departments, vendors, and ISAC partners. Has the organization published information for all workforce members, regarding reporting computer anomalies and incidents to the incident handling team. Such information should be included in routine employee awareness activities. Has the organization planned and conducted routine incident response exercises and scenarios for the workforce involved in the incident response to maintain awareness and comfort in responding to real world threats. Exercises should test communication channels, decision making, and incident responders technical capabilities using tools and data available to them. Has the organization created incident scoring and prioritization schema based on known or potential impact to your organization. Utilize score to define frequency of status updates and escalation procedures. Has the organization established a program for penetration tests that includes a full scope of blended attacks, such as wireless, client-based, and web application attacks. CIS Controls Measures and Metrics for Version 7 Sub--Control Title Description 20.3 Perform Periodic Red Team Exercises 20.4 Include Tests for Presence of Unprotected System Information and Artifacts 20.5 Create Test Bed for Elements Not Typically Tested in Production 20.6 Use Vulnerability Scanning and Penetration Testing Use vulnerability scanning and penetration testing tools in concert. The results of vulnerability scanning Tools in Concert assessments should be used as a starting point to guide and focus penetration testing efforts. Penetration Testing Plans 20.7 Ensure Results from Penetration Test are Documented Using Open, Machine-readable Standards Penetration Testing Plans 20.8 Control and Monitor Accounts Associated with Penetration Testing Contact Information CIS 31 Tech Valley Drive East Greenbush, NY 12061 518.266.3460 controlsinfo@cisecurity.org Conduct regular external and internal penetration tests to identify vulnerabilities and attack vectors that can be used to exploit enterprise systems successfully. Perform periodic Red Team exercises to test organizational readiness to identify and stop attacks or to respond quickly and effectively. Include tests for the presence of unprotected system information and artifacts that would be useful to attackers, including network diagrams, configuration files, older penetration test reports, e-mails or documents containing passwords or other information critical to system operation. Create a test bed that mimics a production environment for specific penetration tests and Red Team attacks against elements that are not typically tested in production, such as attacks against supervisory control and data acquisition and other control systems. Sensor 20.2 Conduct Regular External and Internal Penetration Tests Wherever possible, ensure that Red Teams results are documented using open, machine-readable standards (e.g., SCAP). Devise a scoring method for determining the results of Red Team exercises so that results can be compared over time. Any user or system accounts used to perform penetration testing should be controlled and monitored to make sure they are only being used for legitimate purposes, and are removed or restored to normal function after testing is over. Penetration Testing Plans Penetration Testing Plans Penetration Testing Plans Penetration Testing Plans Penetration Testing Plans Measure Has the organization conducted regular external and internal penetration tests to identify vulnerabilities and attack vectors that can be used to exploit enterprise systems successfully. Has the organization performed periodic Red Team exercises to test organizational readiness to identify and stop attacks or to respond quickly and effectively. Has the organization included tests for the presence of unprotected system information and artifacts that would be useful to attackers, including network diagrams, configuration files, older penetration test reports, e-mails or documents containing passwords or other information critical to system operation. Has the organization created a test bed that mimics a production environment for specific penetration tests and Red Team attacks against elements that are not typically tested in production, such as attacks against supervisory control and data acquisition and other control systems. Has the organization used vulnerability scanning and penetration testing tools in concert. The results of vulnerability scanning assessments should be used as a starting point to guide and focus penetration testing efforts. Has the organization, wherever possible, ensured that Red Teams results are documented using open, machinereadable standards (e.g., SCAP). Devise a scoring method for determining the results of Red Team exercises so that results can be compared over time. Has the organization ensured that any user or system accounts used to perform penetration testing should be controlled and monitored to make sure they are only being used for legitimate purposes, and are removed or restored to normal function after testing is over. Sigma Level One Sigma Level Two Sigma Level Sigma Sigma Three Level Four Level Five No Yes No Yes No Yes No Yes No Yes No Yes No Yes Sigma Level Six License for Use This work is licensed under a Creative Commons Attribution-Non Commercial-No Derivatives 4.0 International Pub nd/4.0/legalcode To further clarify the Creative Commons license related to the CIS ControlsTM content, you are authorized to copy outside of your organization for non-commercial purposes only, provided that (i) appropriate credit is given to CIS, a the CIS Controls, you may not distribute the modified materials. Users of the CIS Controls framework are also requ order to ensure that users are employing the most up to date guidance. Commercial use of the CIS Controls is subj erivatives 4.0 International Public License (the link can be found at https://creativecommons.org/licenses/by-nc- ent, you are authorized to copy and redistribute the content as a framework for use by you, within your organization and ropriate credit is given to CIS, and (ii) a link to the license is provided. Additionally, if you remix, transform or build upon ontrols framework are also required to refer to (http://www.cisecurity.org/controls/) when referring to the CIS Controls in use of the CIS Controls is subject to the prior approval of CIS® (Center for Internet Security, Inc.).